Advances, Systems and Applications

- Search by keyword
- Search by citation
Page 1 of 14

Predicting UPDRS in Parkinson’s disease using ensembles of self-organizing map and neuro-fuzzy
Parkinson's Disease (PD) is a complex, degenerative disease that affects nerve cells that are responsible for body movement. Artificial Intelligence (AI) algorithms are widely used to diagnose and track the pr...
- View Full Text
A cloud-edge computing architecture for monitoring protective equipment
The proper use of protective equipment is very important to avoid fatalities. One sector in which this has a great impact is that of construction sites, where a large number of workers die each year. In this s...
A cloud-edge collaborative task scheduling method based on model segmentation
With the continuous development and combined application of cloud computing and artificial intelligence, some new methods have emerged to reduce task execution time for training neural network models in a clou...
Analysis and prediction of virtual machine boot time on virtualized computing environments
Starting a virtual machine (VM) is a common operation in cloud computing platforms. In order to achieve better management of resource provisioning, a cloud platform needs to accurately estimate the VM boot tim...
IoT workload offloading efficient intelligent transport system in federated ACNN integrated cooperated edge-cloud networks
Intelligent transport systems (ITS) provide various cooperative edge cloud services for roadside vehicular applications. These applications offer additional diversity, including ticket validation across transp...
Intelligent code search aids edge software development
The growth of multimedia applications poses new challenges to software facilities in edge computing. Developers must effectively develop edge computing software to accommodate the rapid expansion of multimedia...
Correction to: Advanced series decomposition with a gated recurrent unit and graph convolutional neural network for non‑stationary data patterns
The original article was published in Journal of Cloud Computing 2024 13 :20
PMNet: a multi-branch and multi-scale semantic segmentation approach to water extraction from high-resolution remote sensing images with edge-cloud computing
In the field of remote sensing image interpretation, automatically extracting water body information from high-resolution images is a key task. However, facing the complex multi-scale features in high-resoluti...
Correction: FLM-ICR: a federated learning model for classification of internet of vehicle terminals using connection records
The original article was published in Journal of Cloud Computing 2024 13 :57
CG-PBFT: an efficient PBFT algorithm based on credit grouping
Because of its excellent properties of fault tolerance, efficiency and availability, the practical Byzantine fault tolerance (PBFT) algorithm has become the mainstream consensus algorithm in blockchain. Howeve...
Time-aware outlier detection in health physique monitoring in edge-aided sport education decision-makings
The increasing popularity of various intelligent sensor and mobile communication technologies has enabled quick health physique sensing, monitoring, collection and analyses of students, which significantly pro...
Accurate and fast congestion feedback in MEC-enabled RDMA datacenters
Mobile edge computing (MEC) is a novel computing paradigm that pushes computation and storage resources to the edge of the network. The interconnection of edge servers forms small-scale data centers, enabling ...
Optimus: association-based dynamic system call filtering for container attack surface reduction
While container adoption has witnessed significant growth in facilitating the operation of large-scale applications, this increased attention has also attracted adversaries who exploit numerous vulnerabilities...
A secure cross-domain authentication scheme based on threshold signature for MEC
The widespread adoption of fifth-generation mobile networks has spurred the rapid advancement of mobile edge computing (MEC). By decentralizing computing and storage resources to the network edge, MEC signific...
Edge intelligence empowered delivery route planning for handling changes in uncertain supply chain environment
Traditional delivery route planning faces challenges in reducing logistics costs and improving customer satisfaction with growing customer demand and complex road traffic, especially in uncertain supply chain ...
Security issues of news data dissemination in internet environment
With the rise of artificial intelligence and the development of social media, people's communication is more convenient and convenient. However, in the Internet environment, the untrue dissemination of news da...
Short-term forecasting of surface solar incident radiation on edge intelligence based on AttUNet
Solar energy has emerged as a key industry in the field of renewable energy due to its universality, harmlessness, and sustainability. Accurate prediction of solar radiation is crucial for optimizing the econo...
Edge computing-oriented smart agricultural supply chain mechanism with auction and fuzzy neural networks
Powered by data-driven technologies, precision agriculture offers immense productivity and sustainability benefits. However, fragmentation across farmlands necessitates distributed transparent automation. We d...
AIoT-driven multi-source sensor emission monitoring and forecasting using multi-source sensor integration with reduced noise series decomposition
The integration of multi-source sensors based AIoT (Artificial Intelligence of Things) technologies into air quality measurement and forecasting is becoming increasingly critical in the fields of sustainable a...
An integrated SDN framework for early detection of DDoS attacks in cloud computing
Cloud computing is a rapidly advancing technology with numerous benefits, such as increased availability, scalability, and flexibility. Relocating computing infrastructure to a network simplifies hardware and ...
An optimized neural network with AdaHessian for cryptojacking attack prediction for Securing Crypto Exchange Operations of MEC applications
Bitcoin exchange security is crucial because of MEC's widespread use. Cryptojacking has compromised MEC app security and bitcoin exchange ecosystem functionality. This paper propose a cutting-edge neural netwo...
Privacy-preserving federated learning based on partial low-quality data
Traditional machine learning requires collecting data from participants for training, which may lead to malicious acquisition of privacy in participants’ data. Federated learning provides a method to protect p...
A secure data interaction method based on edge computing
Deep learning achieves an outstanding success in the edge scene due to the appearance of lightweight neural network. However, a number of works show that these networks are vulnerable for adversarial examples,...
TCP Stratos for stratosphere based computing platforms
Stratosphere computing platforms (SCPs) benefit from free cooling but face challenges necessitating transmission control protocol (TCP) re-design. The redesign should be considered due to stratospheric gravity...
Optimizing the resource allocation in cyber physical energy systems based on cloud storage and IoT infrastructure
Given the prohibited operating zones, losses, and valve point effects in power systems, energy optimization analysis in such systems includes numerous non-convex and non-smooth parameters, such as economic dis...
SRA-E-ABCO: terminal task offloading for cloud-edge-end environments
The rapid development of the Internet technology along with the emergence of intelligent applications has put forward higher requirements for task offloading. In Cloud-Edge-End (CEE) environments, offloading c...
FLM-ICR: a federated learning model for classification of internet of vehicle terminals using connection records
With the rapid growth of Internet of Vehicles (IoV) technology, the performance and privacy of IoV terminals (IoVT) have become increasingly important. This paper proposes a federated learning model for IoVT c...
The Correction to this article has been published in Journal of Cloud Computing 2024 13 :75
Multi-dimensional resource allocation strategy for LEO satellite communication uplinks based on deep reinforcement learning
In the LEO satellite communication system, the resource utilization rate is very low due to the constrained resources on satellites and the non-uniform distribution of traffics. In addition, the rapid movement...
Edge-cloud computing oriented large-scale online music education mechanism driven by neural networks
With the advent of the big data era, edge cloud computing has developed rapidly. In this era of popular digital music, various technologies have brought great convenience to online music education. But vast da...
RNA-RBP interactions recognition using multi-label learning and feature attention allocation
In this study, we present a sophisticated multi-label deep learning framework for the prediction of RNA-RBP (RNA-binding protein) interactions, a critical aspect in understanding RNA functionality modulation a...
Low-cost and high-performance abnormal trajectory detection based on the GRU model with deep spatiotemporal sequence analysis in cloud computing
Trajectory anomalies serve as early indicators of potential issues and frequently provide valuable insights into event occurrence. Existing methods for detecting abnormal trajectories primarily focus on compar...
AI-empowered mobile edge computing: inducing balanced federated learning strategy over edge for balanced data and optimized computation cost
In Mobile Edge Computing, the framework of federated learning can enable collaborative learning models across edge nodes, without necessitating the direct exchange of data from edge nodes. It addresses signifi...
Automated visual quality assessment for virtual and augmented reality based digital twins
Virtual and augmented reality digital twins are becoming increasingly prevalent in a number of industries, though the production of digital-twin systems applications is still prohibitively expensive for many s...
Detection of cotton leaf curl disease’s susceptibility scale level based on deep learning
Cotton, a crucial cash crop in Pakistan, faces persistent threats from diseases, notably the Cotton Leaf Curl Virus (CLCuV). Detecting these diseases accurately and early is vital for effective management. Thi...
Unified ensemble federated learning with cloud computing for online anomaly detection in energy-efficient wireless sensor networks
Anomaly detection in Wireless Sensor Networks (WSNs) is critical for their reliable and secure operation. Optimizing resource efficiency is crucial for reducing energy consumption. Two new algorithms developed...
Edge intelligence-assisted animation design with large models: a survey
The integration of edge intelligence (EI) in animation design, particularly when dealing with large models, represents a significant advancement in the field of computer graphics and animation. This survey aim...
Target tracking using video surveillance for enabling machine vision services at the edge of marine transportation systems based on microwave remote sensing
Automatic target tracking in emerging remote sensing video-generating tools based on microwave imaging technology and radars has been investigated in this paper. A moving target tracking system is proposed to ...
Multiple objectives dynamic VM placement for application service availability in cloud networks
Ensuring application service availability is a critical aspect of delivering quality cloud computing services. However, placing virtual machines (VMs) on computing servers to provision these services can prese...
Investigation on storage level data integrity strategies in cloud computing: classification, security obstructions, challenges and vulnerability
Cloud computing provides outsourcing of computing services at a lower cost, making it a popular choice for many businesses. In recent years, cloud data storage has gained significant success, thanks to its adv...
A secure and efficient electronic medical record data sharing scheme based on blockchain and proxy re-encryption
With the rapid development of the Internet of Medical Things (IoMT) and the increasing concern for personal health, sharing Electronic Medical Record (EMR) data is widely recognized as a crucial method for enh...
A fog-edge-enabled intrusion detection system for smart grids
The Smart Grid (SG) heavily depends on the Advanced Metering Infrastructure (AMI) technology, which has shown its vulnerability to intrusions. To effectively monitor and raise alarms in response to anomalous a...
Enhanced mechanism to prioritize the cloud data privacy factors using AHP and TOPSIS: a hybrid approach
Cloud computing is a new paradigm in this new cyber era. Nowadays, most organizations are showing more reliability in this environment. The increasing reliability of the Cloud also makes it vulnerable. As vuln...
Dynamic routing optimization in software-defined networking based on a metaheuristic algorithm
Optimizing resource allocation and routing to satisfy service needs is paramount in large-scale networks. Software-defined networking (SDN) is a new network paradigm that decouples forwarding and control, enab...
Multi-type concept drift detection under a dual-layer variable sliding window in frequent pattern mining with cloud computing
The detection of different types of concept drift has wide applications in the fields of cloud computing and security information detection. Concept drift detection can indeed assist in promptly identifying in...
Evaluation of AI tools for healthcare networks at the cloud-edge interaction to diagnose autism in educational environments
Physical, social, and routine environments can be challenging for learners with autism spectrum disorder (ASD). ASD is a developmental disorder caused by neurological problems. In schools and educational envir...
Predicting the individual effects of team competition on college students’ academic performance in mobile edge computing
Mobile edge computing (MEC) has revolutionized the way of teaching in universities. It enables more interactive and immersive experiences in the classroom, enhancing student engagement and learning outcomes. A...
Transformative synergy: SSEHCET—bridging mobile edge computing and AI for enhanced eHealth security and efficiency
Blockchain technologies (BCT) are utilized in healthcare to facilitate a smart and secure transmission of patient data. BCT solutions, however, are unable to store data produced by IoT devices in smart healthc...
Harmfulness metrics in digital twins of social network rumors detection in cloud computing environment
Social network rumor harm metric is a task to score the harm caused by a rumor by analyzing the spreading range of the rumor, the users affected, the repercussions caused, etc., and then the harm caused by the...

Multiobjective trajectory optimization algorithms for solving multi-UAV-assisted mobile edge computing problem
The Internet of Things (IoT) devices are not able to execute resource-intensive tasks due to their limited storage and computing power. Therefore, Mobile edge computing (MEC) technology has recently been utili...
Graph convolution networks for social media trolls detection use deep feature extraction
This study presents a novel approach to identifying trolls and toxic content on social media using deep learning. We developed a machine-learning model capable of detecting toxic images through their embedded ...
- Editorial Board
- Sign up for article alerts and news from this journal
Annual Journal Metrics
2022 Citation Impact 4.0 - 2-year Impact Factor 4.4 - 5-year Impact Factor 1.711 - SNIP (Source Normalized Impact per Paper) 0.976 - SJR (SCImago Journal Rank)
2023 Speed 10 days submission to first editorial decision for all manuscripts (Median) 116 days submission to accept (Median)
2023 Usage 733,672 downloads 49 Altmetric mentions
- More about our metrics
- ISSN: 2192-113X (electronic)
Benefit from our free funding service

We offer a free open access support service to make it easier for you to discover and apply for article-processing charge (APC) funding.
Learn more here
An overview of cloud computing in SMEs
- Published: 28 April 2021
- Volume 11 , pages 175–188, ( 2021 )
Cite this article
- Jayalaxmi P Shetty ORCID: orcid.org/0000-0003-4214-8962 1 &
- Rajesh Panda 2
2869 Accesses
13 Citations
Explore all metrics
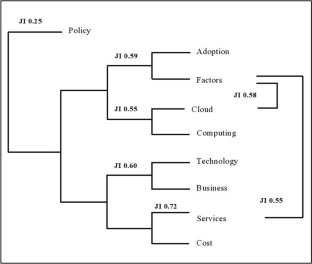
The emergence of the Web in 1990 gave rise to cloud computing; a disruptive innovation in the bird’s-eye view of information technology. Cloud computing essentially sidesteps the need for capital investments in hardware and expensive information technology, yet has many hurdles to overcome. The purpose of this review is to identify the most discussed topics and relevant theories, while also focusing on the influential factors of cloud adoption in small and medium enterprises. This paper provides an investigation of 25 conference papers, articles, and review papers listed in Scopus and 67 articles from popular publications like Emerald Insight, Elsevier, and Sprouts. Articles are comprehended in three stages: (1) word frequency query, (2) cluster analysis, and (3) narrative review. Thus, the research design cumulatively covers 92 articles and uses two review methods; systematic and narrative. The synthesized outcome of the literature identifies four interrelations of topics; cost-services, adoption-factors, technology-business, and cloud-computing, while pinpointing at “policy” as an outlier. Findings highlight the applicability of influential factors such as “cost” and “flexibility” to multiple benefits of cloud computing, both tangible and intangible. The results encapsulate the synthesis of theoretical models (Technological-Organization-Environment framework and Technology Acceptance Model). Other summarizations are their embedded constructs, impediments, and cloud economics. The roles of other stakeholders enhance cluster-wise e-readiness for all-round benefits. Practitioners can leverage cloud benefits to augment successful adoption and diffusion. Researchers can look forward to addressing gaps in the area of policy, risks, and service models to facilitate the business aspect of cloud technology.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Similar content being viewed by others

Digital technologies: tensions in privacy and data
Sara Quach, Park Thaichon, … Robert W. Palmatier
Re-examining the Unified Theory of Acceptance and Use of Technology (UTAUT): Towards a Revised Theoretical Model
Yogesh K. Dwivedi, Nripendra P. Rana, … Michael D. Williams

The theory contribution of case study research designs
Hans-Gerd Ridder
Data availability
Data sharing does not apply to this article as no datasets were generated or analyzed during the current study. This being a literature review article; all publications that are reviewed are provided in the reference.
Association of South-East Asian Nations (ASEAN) comprises of 10 nations; Brunei, Cambodia, Indonesia, Laos, Malaysia, Myanmar, Philippines, Singapore, Thailand, and Vietnam. ASEAN is a global ICT primarily engaged in producing ICT hardware and ICT service exports.
Abbreviations
Association of Southeast Asian Nations
cloud service provider
diffusion of innovation
infrastructure as a service
information and communication technology
infocomm and development authority
innovation diffusion theory
information technology
Information Technology and Broadcasting Bureau
Jaccard’s index
National Telecom Policy
platform as a service
return on investment
software as a service
Technology Acceptance Model
transaction cost economics
total cost of ownership
technological organization environment
theory of planned behavior
theory of reasoned action
small and medium enterprises
willingness to pay
Agostino, A., Søilen, K. S., & Gerritsen, B. (2013). Cloud solution in business intelligence for SMEs -vendor and customer perspectives. Journal of Intelligence Studies in Business, 3 (3), 5–28.
Article Google Scholar
Ajzen, I. (1991). The theory of planned behaviour. Organizational Behavior and Human Decision Processes, 50 (2), 179–211.
Alkhalil, A. (2013). Journal of Information Technology Management A Publication of the Association of Management Cloud Computing : A new phase in information technology management. Journal of Information Technology Management, X, 1 , 2013.
Google Scholar
Alshamaila, Y., Papagiannidis, S., & Li, F. (2013). Cloud computing adoption by SMEs in the northeast of England. Journal of Enterprise Information Management, 26 (3), 250–275.
Ariwa, E., & Ibe, K. C. (2013). Cloud computing sustainability and business process re-engineering in SMEs: Comparative analysis of UK and Nigeria. In Third International Conference on Innovative Computing Technology (INTECH 2013). London, U.K, August 29–31, 2013, IEEE , 181–183.
Assante, D., Castro, M., Hamburg, I., & Martin, S. (2016). The use of cloud computing in SMEs. Procedia Computer Science, 83 , 1207–1212.
Awa, H. O., Ojiabo, O. U., & Emecheta, B. C. (2015). Integrating TAM, TPB, and TOE frameworks and expanding their characteristic constructs for e-commerce adoption by SMEs. Journal of Science and Technology Policy Management, 6 (1), 76–94.
Azam, M. S., & Quaddus, M. (2013). Examining the influence of national culture on adoption and use of information and communication technology: A study from Bangladesh’s SME perspective. The International Technology Management Review, 3 (2), 116–126.
Bagozzi, R. P., Yi, Y., & Phillips, L. W. (1991). Assessing construct validity in organizational research. Administrative Science Quarterly, 36 (3), 421–458.
Bieber, K., Grivas, S. G., & Giovanoli, C. (2016). Cloud computing business case framework: Introducing a mixed-model business case framework for small and medium enterprises to determine the value of cloud computing. In Proceedings - 3rd International Conference on Enterprise Systems. Basel, Switzerland, October 14–15, 2015, 161–168.
Brender, N., & Markov, I. (2013). Risk perception and risk management in cloud computing: Results from a case study of Swiss companies. International Journal of Information Management, 33 (5), 726–733.
Cervone, H. F. (2010). An overview of virtual and cloud computing. OCLC Systems & Services: International Digital Library Perspectives, 26 (3), 162–165.
Chang, V., Walters, R. J., & Wills, G. (2013). The development that leads to the cloud computing business framework. International Journal of Information Management, 33 , 524–538.
Chong, H.-Y., Wong, J. S., & Wang, X. (2014). An explanatory case study on cloud computing applications in the built environment. Automation in Construction, 44 , 152–162.
Christensen, C. M., Anthony, S. D., & Roth, E. A. (2004). Seeing what’s next: Using theories of innovation to predict industry change . Harvard Business School Press.
Colicchio, C., Giovanoli, C., & Stella, G. G. (2015). A cloud readiness assessment framework for enterprise content management and social software (E-collaboration) in small and medium-sized enterprises. At International Conference on Enterprise Systems (ES) . Basel, Switzerland, October 14–15, 2015, 177–183.
Davis, F. D. (1989). Perceived usefulness, perceived ease of use, and user acceptance of information technology. Management Information Systems Quarterly, 13 (3), 319–340.
Deniz, A., & Kuyucu, H. (2011). Exploring policy-formulation for SMEs in cloud computing: The case of Turkey. IBIMA Business Review, 890061 , 1–13.
DePietro, R., Wiarda, E., & Fleischer, M. (1990).The context for change: Organization, technology, and environment. The Process of Technological Innovation, Lexington Books . Lexington, MA , 51-175.
Dickerson, M. D., & Gentry, J. W. (1983). Characteristics of adopters and non-adopters of home computers. The Journal of Consumer Research, 10 (2), 225–235.
Doherty, E., Carcary, M., & Conway, G. (2015). Migrating to the cloud. Journal of Small Business and Enterprise Development, 22 (3), 512–527.
El Garah, W., Berrado, A., & El Ouarti, N. (2010). Cloud computing adoption in an emerging market. In Business Transformation through Innovation and Knowledge Management: An Academic Perspective - Proceedings of the 14th International Business Information Management Association Conference, IBIMA 2010 , 2 , 1310–1313.
Faasen, J., Seymour, L. F., & Schuler, J. (2013). Enterprise Information Systems of the Future . (G. Poels, Ed.) Lecture Notes in Business Information Processing, Springer ,139. Berlin Heidelberg.
Fishbein, M., & Ajzen, I. (1975). Belief, attitude, intention, and behavior: An introduction to theory and research . Addison-Wesley.
Gangwar, H., Date, H., & Raoot, A. D. (2014). Review on IT adoption: Insights from recent technologies. Journal of Enterprise Information Management, 27 (4), 488–502.
Gatignon, H., & Robertson, T. S. (1985). A propositional inventory for new diffusion research. Journal of Consumer Research, 11 (March), 849–867.
Gerhardter, A., & Ortner, W. (2013). Innovation and future of enterprise information systems. (F. Piazolo & M. Felderer, Eds.) Lecture Notes in Information Systems and Organisation , Springer , 4 . Berlin, Heidelberg.
Ghobakhloo, M., & Hong Tang, S. (2013). The role of owner/manager in the adoption of electronic commerce in small businesses. Journal of Small Business and Enterprise Development, 20 (4), 754–787.
Giovannis, A. N., Binioris, S., & Polychronopoulos, G. (2012). An extension of the TAM model with IDT and security/privacy risk in the adoption of internet banking services in Greece. EuroMed Journal of Business, 7 (1), 24–53.
Gounaris, S., & Koritos, C. (2008). Investigating the drivers of internet banking adoption decision -A comparison of three alternative frameworks. International Journal of Bank Marketing, 26 (5), 282–304.
Grubisic, I. (2014). ERP in clouds or still below. Journal of Systems and Information Technology, 16 (1), 62–76.
Gupta, P., Seetharaman, A., & Raj, J. R. (2013). The usage and adoption of cloud computing by small and medium businesses. International Journal of Information Management, 33 , 861–874.
Gutierrez, A., Boukrami, E., & Lumsden, R. (2015). Technological, organizational, and environmental factors influencing managers’ decision to adopt cloud computing in the UK. Journal of Enterprise Information Management, 28 (6), 788–807.
Haleem, A., Mannan, B., Luthra, S., Kumar, S., & Khurana, S. (2018). Technology forecasting (TF) and technology assessment (TA) methodologies : A conceptual review. Benchmarking: An International Journal, 26 (1), 48–72.
Heeks, R. (2002). Information systems and developing countries : Failure, success, and local improvisations. The Information Society, 18 , 101–112.
Herrera, A., & Janczewski, L. (2014). Issues in the study of organizational resilience in cloud computing environments. Procedia Technology, 16 , 32–41.
Hsu, P. F., Ray, S., & Li-Hsieh, Y. Y. (2014). Examining cloud computing adoption intention, pricing mechanism, and deployment model. International Journal of Information Management, 34 , 474–488.
Javalgi, R. R. G., & Todd, P. R. (2011). Entrepreneurial orientation, management commitment, and human capital: The internationalization of SMEs in India. Journal of Business Research, 64 (9), 1004–1010.
Jede, A., & Teuteberg, F. (2015). Integrating cloud computing in supply chain processes. Journal of Enterprise Information Management, 28 (6), 872–904.
Jede, A., & Teuteberg, F. (2016). Towards cloud-based supply chain processes. The International Journal of Logistics Management, 27 (2), 438–462.
Kannabiran, G., & Dharmalingam, P. (2012). Enablers and inhibitors of advanced information technologies adoption by SMEs. Journal of Enterprise Information Management, 25 (2), 186–209.
Karunakaran, S., Krishnaswamy, V., Rangaraja, P., & S. (2015). Business view of cloud. Management Research Review, 38 (6), 582–604.
Kramer, F. (2014). On the advantages, perils, and pitfalls of using cloud computing and open-source software in small and medium-sized businesses. The case of a german entrepreneurial company. In the 20th Americas Conference on Information Systems, AMCIS 2014 . Association for Information Systems , Savannah , 1–12.
Kshetri, N. (2015). Institutional and economic factors affecting the development of the Chinese cloud computing industry and market. Telecommunications Policy, 40 (2), 116–129.
Li, M., Yu, Y., Zhao, J. L., & Li, X. (2012). Drivers for strategic choice of cloud computing as online service in SMEs. In ICIS-RP , Orlando, 1–11.
Li, M., Zhao, D., & Yu, Y. (2015). TOE drivers for cloud transformation: Direct or trust-mediated. Asia Pacific Journal of Marketing and Logistics, 27 (2), 226–248.
Lian, J. W., Yen, D. C., & Wang, Y. T. (2014). An exploratory study to understand the critical factors affecting the decision to adopt cloud computing in Taiwan hospital. International Journal of Information Management, 34 , 28–36.
Lonea, A. M., Popescu, D. E., & Proştean, O. (2012). The overall process taken by enterprises to manage IaaS cloud services. In Proceedings of the 6th European Conference on Information Management and Evaluation. Cork, Ireland , September 13-14, 2012, 168–177.
Low, C., Chen, Y., & Wu, M. (2011). Understanding the determinants of cloud computing adoption. Industrial Management & Data Systems, 111 (9), 1006–1023.
Marian, M., & Hamburg, I. (2013). Co-operative e-learning approach based on cloud computing. In Proceedings of the IASTED International Conference. Innsbruck, Austria, February, 13–15, 2013, Web-based Education, 838–843.
Mell, P., & Grance, T. (2010).The NIST definition of cloud computing, available at www. newinnovationsguide.com/NIST_Cloud_Definition.pdf .
Misra, S. C., & Mondal, A. (2011). Identification of a company’s suitability for the adoption of cloud computing and modeling its corresponding return on investment. Mathematical and Computer Modelling, 53 , 504–522.
Moore, G. C., & Benbasat, I. (1991). Development of an instrument to measure the perceptions of adopting an information technology innovation. Information Systems Research, 2 (3), 192–222.
Morgan-Thomas, A. (2015). Rethinking technology in the SME context : Affordances, practices, and ICTs. International Small Business Journal, 34 (8), 1122–1136.
Muhic, M., & Johansson, B. (2014). Cloud sourcing – Next generation outsourcing ? Procedia Technology, 16 , 553–561.
Oliveira, T., & Martins, M. F. (2010). Industrial Management & Data Systems Understanding e-business adoption across industries in European countries. Industrial Management & Data Systems, 110 (3), 1337–1354.
Ostlund, L. E. (1974). Perceived innovation attributes as predictors of innovativeness. The Journal of Consumer Research, 1 (2), 23–29.
Porter, M. E. (1980). Competitive advantage: Creating and sustaining superior performance . New York: Free Press.
Prasad, A., Green, P., & Heales, J. (2014). On governance structures for the cloud computing services and assessing their effectiveness. International Journal of Accounting Information Systems, 15 (4), 335–356.
Priyadarshinee, P., Raut, R. D., Kumar, M., & Kamble, S. S. (2017). A cloud computing adoption in Indian SMEs: Scale development and validation approach. The Journal of High Technology Management Research, 289 (2), 221–245.
Raut, R. D., Gardas, B. B., Narkhede, B. E., & Narwane, V. S. (2019). To investigate the determinants of cloud computing adoption in the manufacturing micro, small, and medium enterprises. Benchmarking: An International Journal, 26 (3), 990–1019.
Ren, L., Zhang, L., Tao, F., Zhao, C., Chai, X., & Zhao, X. (2013). Cloud manufacturing: From concept to practice. Enterprise Information Systems, 9 (2), 186–209.
Rogers, E. M. (1983). Diffusion of innovation . The Free Press.
Rogers, E. M. (1995). Diffusion of innovations (4th ed.). The Free Press.
Ross, P. K., & Blumenstein, M. (2013). Cloud computing: The nexus of strategy and technology. Journal of Business Strategy, 34 (4), 39–47.
Ross, P. K., & Blumenstein, M. (2015). Cloud computing as a facilitator of SME entrepreneurship. Technology Analysis & Strategic Management, 27 (1), 87–101.
Schniederjans, D. G., & Hales, D. N. (2016). Cloud computing and its impact on economic and environmental performance: A transaction cost economics perspective. Decision Support Systems, 86 , 73–82.
Scott, M., & Watson, R. (2012). The value of Green IT: A theoretical framework and exploratory assessment of cloud computing. In the Proceedings of the 25th Bled eConference. Bled, Slovenia , June 17-20, 2012, Paper 30, 294–308.
Shetty, J. P., & Panda, R. (2020). A multidimensional framework for cloud adoption of SMEs in India. International Journal of Indian Culture and Business Management, 20 (2), 210–233.
Singh Kalsi, N., & Kiran, R. (2013). E-governance success factors. International Journal of Public Sector Management, 26 (4), 320–336.
Singh, V., & Singh, G. (2018). Citizen centric assessment framework for e-governance services quality. International Journal of Business Information Systems, 27 (1), 1–20.
Sinha, I., & Sharma, M. K. (2015). Cloud computing in small and medium-sized enterprises: An architectural model. International Journal of Enterprise Network Management, 6 (3), 185.
Snowden, S., Spafford, J., Michaelides, R., & Hopkins, J. (2006). Technology acceptance and m-commerce in an operational environment. Journal of Enterprise Information Management, 19 (2), 525–539.
Sokal, R. R., & Rohlf, F. J. (2017). The comparison of dendrograms by objective methods. Taxon 11. International Association for Plant Taxonomy (IAPT), 11 (2), 33–40.
Soon, J. N. P., Mahmood, A. K., Yin, C. P., Wan, W. S., Yuen, P. K., & Heng, L. E. (2014). IaaS cloud optimization during economic turbulence for Malaysia small and medium enterprises. International Journal of Business Information Systems, 16 (2), 196.
Srinuan, C. (2017) ‘Willingness to pay for cloud computing service of SME in Thailand’, Paper presented at 3rd International Conference on Information Management , IEEE, Chengdu, China, April, 21–23, 2017, 21–25.
Subrahmanya, M. H. B. (2007). Development strategies for Indian SMEs: Promoting linkages with global transnational corporations. Management Research News, 30 (10), 762–774.
Subramanian, N., Abdulrahman, M. D., & Zhou, X. (2014). Integration of logistics and cloud computing service providers: Cost and green benefits in the Chinese context. Transportation Research Part E: Logistics and Transportation Review, 70 , 86–98.
Sultan, N. A. (2011). Reaching for the “cloud”: How SMEs can manage. International Journal of Information Management, 31 (3), 272–278.
Sultan, N. (2013). Cloud computing: A democratizing force? International Journal of Information Management, 33 (5), 813–815.
Sultan, N. (2014). Making use of cloud computing for healthcare provision: Opportunities and challenges. International Journal of Information Management, 34 (2), 177–184.
Swanson, E. B. (1994). Information systems innovation among organizations. Management Science, 40 (9), 1069–1092.
Tan, P. N., Steinbach, M., & Kumar, V. (2005). Introduction to data mining . Addison-Wesley.
Tarhini, A., Yunis, M., & El-Kassar, A. N. (2018). Innovative sustainable methodology for managing in-house software development in SMEs. Benchmarking: An International Journal, 25 (3), 1085–1103.
Tornatsky, L., & Fleischer, M. (1990). The process of technology innovation, Lexington Books. Lexington, MA.
Vasiljeva, T., Shaikhulina, S., & Kreslins, K. (2017). Cloud computing: Business perspectives, benefits, and challenges for small and medium enterprises (case of Latvia). Procedia Engineering, 178 , 443–451.
Vidalis, S., & Angelopoulou, O. (2013). Deception and maneuver warfare utilizing cloud resources. Information Security Journal: A Global Perspective, 22 (4), 151–158.
Vidhyalakshmi, R., & Kumar, V. (2016). Determinants of cloud computing adoption by SMEs. International Journal of Business Information Systems, 22 (3), 375–395.
Vu, K. M. (2017). ICT diffusion and production in ASEAN countries: Patterns, performance, and policy directions. Telecommunications Policy, 41 (10), 962–977.
Wach, K. (2020). A typology of small business growth modelling : A critical literature review. Entrepreneurial Business and Economics Review, 8 (1), 159–184.
Walterbusch, M., Martens, B., & Teuteberg, F. (2013). Evaluating cloud computing services from a total cost of ownership perspective. Management Research Review, 36 (6), 613–638.
Wang, F. K., & He, W. (2014). Service strategies of small cloud service providers: A case study of a small cloud service provider and its clients in Taiwan. International Journal of Information Management, 34 , 406–415.
Wonglimpiyarat, J. (2014). Innovative policies to support technology and ICT development. Government Information Quarterly, 31 (3), 466–475.
Xu, Z. (2018). Small and medium enterprises innovation management system based on clustering algorithm. Wireless Personal Communications, 102 (4), 2885–2896.
Yan, H., Hua, Q., Wang, Y., Wei, W., & Imran, M. (2017). Cloud robotics in smart manufacturing environments: Challenges and countermeasures. Computers and Electrical Engineering, 63 , 56–65.
Yang, H., & Tate, M. (2012). A descriptive literature review and classification of cloud computing research. Communications of the Association for Information Systems, 31 , 35–60.
Zhu, K., Kraemer, K. L., Xu, S., & Dedrick, J. (2004). Information technology payoff in E-business environments: An international perspective on value creation of E-business in the financial services industry. Journal of Management Information Systems, 21 (1), 17–54.
Download references
Author information
Authors and affiliations.
Management Faculty, Symbiosis International (Deemed University), Lavale, Mulshi Taluk, Pune, Maharashtra, 412115, India
Jayalaxmi P Shetty
Xavier Institute of Management, Xavier University, Xavier Square, Bhubaneswar, 751 013, India
Rajesh Panda
You can also search for this author in PubMed Google Scholar
Contributions
In this review, the authors have taken stock of the most discussed topics and identified relevant theories for cloud adoption. The study has a 2-fold goal; one is to guide the cash-strapped SME towards advancement, through information technology and the other to contribute to the research knowledge bank. JPS carried out the research as her ongoing doctoral thesis under the close supervision of her supervisor and co-author, RP. Both authors read and approved the manuscript.
Corresponding author
Correspondence to Jayalaxmi P Shetty .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Rights and permissions
Reprints and permissions
About this article
Shetty, J.P., Panda, R. An overview of cloud computing in SMEs. J Glob Entrepr Res 11 , 175–188 (2021). https://doi.org/10.1007/s40497-021-00273-2
Download citation
Received : 07 December 2019
Accepted : 28 February 2021
Published : 28 April 2021
Issue Date : December 2021
DOI : https://doi.org/10.1007/s40497-021-00273-2
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Cloud computing
- Cluster analysis
- Narrative review
- Small and medium enterprise
- Systematic review
- Find a journal
- Publish with us
- Track your research
IEEE Account
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
- We're Hiring!
- Help Center
Cloud Computing
- Most Cited Papers
- Most Downloaded Papers
- Newest Papers
- Save to Library
- Last »
- Access Control Follow Following
- VoIP/SIP/IMS Follow Following
- Distributed Information Systems Follow Following
- Cyber Physical Systems Follow Following
- Semantic Computing Follow Following
- P2P/Overlay Networks Follow Following
- Smart spaces Follow Following
- Complex Event Processing Follow Following
- Cyber Security Follow Following
- Data Mining Follow Following
Enter the email address you signed up with and we'll email you a reset link.
- Academia.edu Publishing
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
- Paper Writer Free >
- Essays Examples >
- Essay Topics >
Cloud Computing Research Paper Samples
Type of paper: Research Paper
Topic: Cloud , Computers , Cloud Computing , Technology , Business , System , Company , Information
Words: 2750
Published: 2020/12/27
This paper discusses cloud computing based on Enterprise Resource Planning (ERP). The cloud computing processing system has become one of the fastest growing areas in the field of Information Technology. The prime purpose of cloud computing is to share the available resources so that economies of scale can be achieved rather than completely relying on the local servers to handle the information technology applications. This paper discusses the major milestones achieved by cloud computing with reference to three organizations that have successfully implemented cloud computing and have achieved satisfactory results. There are many drawbacks and benefits associated with cloud-based ERP system which have been discussed further in this paper. When we analyze the importance of cloud computing as compared to traditional ERP system, it is clear that cloud computing helps in achieving economies of scale through reducing operating and total upfront costs of business processes. This technology is of utmost importance because it is a recent evolution in the field of Information Technology.
Introduction
Since the beginning, the wide majority of the Enterprise Resource Planning System has been based on the principles. The traditional ERP systems does provide different benefits such as more customization, mature functionality of the processing system along with a well-integrated system. Since past few decades, various software applications have been converted to cloud computing that has become one of the fastest growing areas in the field of Information Technology. Cloud computing reveals the next generation processing system (Guido, 2014). Cloud Computing The cloud computing processing system has become one of the fastest growing areas in the field of Information Technology. The prime purpose of cloud computing is to share the available resources so that economies of scale can be achieved rather than completely relying on the local servers to handle the information technology applications. The name of cloud computing results from “cloud” which is used as an allegory for the Internet. Therefore, the term cloud computing means computing that is internet based. With the help of cloud computing, various applications and storage servers are transferred from one computer to another with the help of an Internet (Guido, 2014). The resources and applications that are used by cloud computing are used in two major ways. First, they can be relocated as per demand of the user and second they can be shared by multiple users at the same time. This can be understood with an example that a cloud computing system that is used in North America during the business hours and utilizes the services of Outlook, same resources can be used for the European country users during their business hours. The only difference is that in European country the application is changed such as the web server used in cloud computing will be different than the one used earlier for North American clients (Guido, 2014). The application of using same applications not only help in reducing the impact of environmental damage and utilize energy efficient resources but also help the company to reap economies of scale, save costs, reduce rack space and also eliminate repetitive processes. Another benefit of this technology is that multiple users can have access to a same server and update their storage data and information without having to buy licenses to access different applications and online storage facility. When an organization plans to shift to cloud computing it will be transferring its resources from the traditional Capex technology to Opex model that applies the concept of shared resources and applications (Guido, 2014).
Milestones in progress of cloud computing
The concept behind this popular technology was launched in 1960’s and since then cloud computing has progressed in the field of Information Technology that there is no looking back. The evolution of Web 2.0 is the latest development in the field. Cloud computing was launched late for the web developers even though while 1990’s the Internet had started to use major bandwidth (Guido, 2014). The launch of Salesforce.com is considered to be one of the main milestones of cloud computing in late 1990’s era which helped in the development of an enterprise application with a website that was simple to use and user-friendly. This assisted both the software development professionals and the software companies to develop applications that can deliver software online. The next milestone was the launch of Amazon.com with its remarkable and user-friendly web services. This was a major hit in 21st century which provided a successful and integral medium for cloud computing that provided effective storage services, computation and human intelligence (Guido, 2014). The third main milestone was the development of Elastic Compute Cloud by Amazon.com. This was a business opportunity for small to medium size organizations as well as individuals to rent computers for their personal usage. Another milestone was the launch of Web 2.0 that occurred in 2009 which was extremely successful in the form of Google.com and many other organizations started providing the services of free web browsers. These web browsers supported enterprise resource planning application with the assistance of Google Application. Since then the milestones have been achieved to a greater degree with the most successful one being various applications developed by the Microsoft and Google that are considered to be technology giants in an industry (Ivanus, 2014).
Practical examples of cloud computing
It is important that before discussing the benefits and drawbacks of cloud computing in details as far as Enterprise Resource Planning is concerned, we discuss some of the practical examples of cloud computing and three organizations that have implemented this latest technology. One organization that has implemented cloud computing is Hartford that delivers Information Technology services to its users. With the launch of cloud computing into the company’s technological system, the infrastructure has dominantly changed, and the company also provides personal cloud computing services to its users. Hartford organization focuses on property business, mutual fund, etc. for the implementation of amalgamated model of Information Technology that will definitely help the company to meet customers need and requirements. This will also help to reap economies of scale through cost reduction and improvement in overall performance with support for cloud computing. The second organization that is practically experiencing cloud computing is Delhaize America. This organization has various grocery chains that are managing a huge amount of data with the support and management of cloud computing. The technology of cloud computing helps in studying the impact of weather on sales and various product category in stores. Since cloud computing is successfully implemented in this company, it has been able to diagnose that when the weather is warm, it will result in reduce sale of meat especially the grilled one and increase the sale of newspapers and different magazines. This insight helps the company to make a right decision regarding what to stock, how to promote products, offer discounts, etc. This organization has implemented SoftLayer cloud computing infrastructure that is well-integrated with the Information Technology system (Babcock, 2011). The third company that will be discussed in this paper that has implemented cloud computing is Pearson company which is utilizing the services of cloud computing to provide high-quality education across the globe. This technology has enabled Pearson to develop global hybrid infrastructure that helps provide same infrastructure and processes. This will eventually help the company to free up resources that are not required and invest in the new ones and focus on providing online education that will help in improving the concepts and performance of the learners (Babcock, 2011).
Shift from traditional ERP to cloud ERP computing
The cloud computing that is based on Enterprise Resource Planning as mentioned above has become the fastest growing and the most popular area in the field of Information Technology. Hence, the shift from the traditional means of ERP to cloud computing is quite obvious. There are many drawbacks and benefits associated with cloud-based ERP system which will be discussed further in this paper. When we analyze the importance of cloud computing as compared to traditional ERP system, it is clear that cloud computing helps in achieving economies of scale through reducing operating and total upfront costs of business processes. The major reason behind this cost reduction is that organizations do not have to invest heavily in Information Technology upfront with cloud computing. Unlike the traditional Enterprise Resource Planning system the cloud-based ERP can be configured and adjusted according to client demand, can be replicated and maintained at a rapid level, which means it can deliver more and help in better utilization of the infrastructure that is required for computing. This again leads to the main benefit of cloud computing – reduction in total upfront and operating costs. Another advantage of shifting from traditional ERP to cloud-based ERP is that cloud-based computing can be rapidly invested and well-integrated with organization’s infrastructure as compared to traditional ERP system which needs more resources, time and effort (Jonathan, 2012).
Benefits of cloud computing in ERP
This technology is of utmost importance because it is a recent evolution in the field of Information Technology. The resources and applications that are used by cloud computing are used in two major ways. First, they can be relocated as per the demand of the user and second they can be shared by multiple users at the same time. The application of using same applications not only help in reducing the impact of environmental damage and utilize energy efficient resources, but also helps the company to reap economies of scale, save costs, reduce rack space and also eliminate repetitive processes (Ivanus, 2014). Another benefit of this technology is that multiple users can have access to a same server and update their stored data and information without having to buy licenses to access different applications and online storage facility. Even though, the implementation of cloud computing would mean reaping economies of scale, reduction in costs and time-saving it also means transformation of the business. It is not only implemented in small and medium size companies, but also in large organizations and government sector (Ivanus, 2014). Some major benefits of cloud computing are: The earlier model of IT focused upon the concept that if a software or an application is not performing properly only then it should be fixed. Due to this problem, the businesses had to suffer due to time wastage in downtime of resources and lack of effective skills to handle crisis management situation. The benefit of cloud computing is that it provides timely updates of the issues with equipment so that the problems are handled on time to save time wasted to recover and fix the resources (Srinivisan, 2014). The application of using same applications not only help in reducing the impact of environmental damage and utilize energy efficient resources, but also helps the company to reap economies of scale, save costs, reduce rack space and also eliminate repetitive processes (Joe, 2013). It reduces the upfront and operational costs for the business processes as it reduces the overall expenses that are incurred by an organization to implement Enterprise Resource Planning System or to switch to a new cloud-based system based on new technology. This provides more benefit to small to medium sized organizations. Along with lower upfront costs, the overall operational costs are also reduced, which means energy costs, costs of upgrading a system, configuring and maintenance (Srinivisan, 2014). The cloud-based ERP system can be quickly implemented in an organization as compared to the traditional ERP system. The companies can also change the cloud service providers more quickly and reduce the service type that is required to provide more products and services to different kind of business structures. The cloud-based ERP system remains focused on utilizing the resources to an extent that the core competence of an organization remains focused upon. In many cases, the cloud based ERP system helps to reduce pressure on internal department of Information Technology that’s major area is to focus on providing core competency in IT services. Since small medium enterprises have limited resources they cannot invest in advanced technology, but with the help of cloud computing they also have access to specialized technology and latest computing resources. Cloud ERP computing system provides faster updates and more functions as compared to traditional ERP system. It also provides improved usability and accessibility. Apart from this, the cloud-based ERP system is user-friendly and usable as compared to traditional ERP system (Srinivisan, 2014). It also provides a convenient integration with different cloud computing services. Once an organization has implemented SaaS cloud computing services it can adopt other cloud ERP computing services at very cheap rates once the cloud service providers have integrated their product with that of the company’s (Benlian, 2011). This also helps in backup, disaster recovery and improved recovery procedures in a better way as compared to traditional ERP system.
Drawbacks of cloud computing in ERP
There are two sides of a coin and this technology also comes with various drawbacks that will be discussed below: An overt fact of cloud computing based on ERP is that additional subscription fees are charged for the product that do not reduce or remain fixed over time, in fact, this fees increases with time as compared to the overall capital investment that is involved in traditional ERP software system. One major drawback of this application is that it has serious confidentiality and security risks as compared to traditional ERP software. This risk is also controversial as some persist that confidentiality and security risks are well taken care of by application developers. Hence, these risks are relatively more prominent and significant when large organizations adopt cloud computing as compared to small-to-medium organizations (Jonathan, 2012). There is a certain amount of performance risk associated with cloud-based computing in ERP software as compared to traditional ERP system, but this performance risk prevails with every software. The performance risk associated with cloud based computing is related to reliability of the network, computing speed, certain limitations of the data transfer facility and other risks involved. Even though an integration process with another cloud computing services is easy and possible as compared to other software applications, but there are certain limitations involve that overcome the beauty of the product. There have been certain constraints that have been noticed regarding interoperability of cloud computing with its home-based applications and integration of its services with existing portfolios and Information Technology platforms. Unlike the traditional ERP processes, cloud computing at times does not support the detail customization and integration with third-party services which becomes difficult for the user to handle (Jonathan, 2012). Since usually the Information Technology departments are outsourced in various organizations, they may lose some of their core competence in IT as well as might experience resistance towards changes in the organization. These issues become more prominent in large organizations as compared to medium to small companies. Since the cloud ERP system is new and is not mature like the traditional ERP system they may have some hitches in the system and may not function as maturely as to satisfy all the office needs of an organization to compete in an industry. There are certain limitations involved in the use of hybrid deployment strategy that may be needed to integrate Enterprise Resource Planning with the local office processes, retain its legacy system if required and third overcome any deficiency that exists within public networks of government sectors (Jonathan, 2012). Many a times it gets to difficult to define the service agreements between corporate clients and cloud computing as these service agreements do not cover security risks and confidentiality concerns that may damage the liability of organizations later on.
Future of cloud computing
The future of cloud computing is extremely promising and successful. Various researches have predicted that till the year 2020, more than half of all the web services, applications and software will be transferred to cloud computing systems. If we estimate currently, around 55 percent of organizations consider that cloud computing technology differentiates them from their competitors and provide them with competitive advantage, whereas more than 55 percent of organizations spend their annual budget of 10 percent on transforming their applications to cloud computing services (Winfrey, 2013). According to different researches that till 2020 more than 7.5 billion mobile devices will follow the latest trend of cloud computing. The software that will be used in cloud computing will be easily accessible with one tap as this technological advancement will help to deploy applications and softwares quickly. This will not only lead to technological advancement but also provide quick response time to different applications (Winfrey, 2013).
The cloud computing processing system has become one of the fastest growing areas in the field of Information Technology. The prime purpose of cloud computing is to share the available resources so that economies of scale can be achieved rather than completely relying on the local servers to handle the information technology applications. The cloud computing that is based on Enterprise Resource Planning as mentioned above has become the fastest growing and the most popular area in the field of Information Technology. Hence, the shift from the traditional means of ERP to cloud computing is quite obvious. Unlike the traditional Enterprise Resource Planning system the cloud-based ERP can be configured and adjusted according to client demand, can be replicated and maintained at a rapid level, which means it can deliver more and help in better utilization of the infrastructure that is required for computing. There are many drawbacks and benefits associated with cloud computing. This technology is of utmost importance because it is a recent evolution in the field of Information Technology.
Babcock C. (2011) 4 Companies Getting Real Results From Cloud Computing, Information Week http://www.informationweek.com/4-companies-getting-real-results-from-cloud-computing/d/d-id/1095455. Benlian A. & Hess T. (2011) Opportunities and risks of SaaS. Findings from a survey of IT executives. Decision Support Systems, Vol. 52: p.232. Guido P. (2014) A More Connected World: How The Cloud Is Boosting Global Travel And Trade, Forbes.com http://www.forbes.com/sites/ibm/2014/10/30/a-more-connected-world-how-the-cloud-is-boosting-global-travel-and-trade/ Ivanus et al. (2014) Cloud Computing Technology Trends, Fiability & Durability, Issue 1, p.26. Joe M. (2013) 5 Benefits Of Cloud Computing You Aren't Likely To See In A Sales Brochure, Forbes.com, http://www.forbes.com/sites/joemckendrick/2013/07/21/5-benefits-of-cloud-computing-you-arent-likely-to-see-in-a-sales-brochure/ Jonathan. G. (2012) To Cloud Or Not To Cloud: That Is The Question For ERP, MHD Supply Chain Solutions; Vol. 42 Issue 1: pp.36-37 Srinivisan (2014) Cloud Computing Basics, Springer. Winfrey G. (2013) How the Cloud Will Transform Business by 2020, Inc.com.
Share with friends using:
- Example Of Complete Name Of Student Research Paper
- Generation Research Papers
- Radical Essays
- Functionalism Essays
- Liberalism Essays
- Happening Essays
- Dependency Essays
- Microwave Essays
- Baptism Essays
- Greatness Essays
- St Augustine Essays
- Round Table Essays
- Query Essays
- Havoc Essays
- Bade Essays
- Consequence Essays
- Slapstick Essays
- Sister Essays
- Human Immunodeficiency Virus Essays
- Pathogenesis Essays
- Haplotype Essays
- Provirus Essays
- Opportunistic Infection Essays
- Chess Essays
- Sexual Assaults Essays
- Californian Essays
- Enrollment Essays
- Lawsuit Essays
- Viewer Essays
- Jail Essays
- Populace Essays
- Nourishment Essays
- Sparrow Essays
- Trillion Essays
- Gesture Essays
- Trainer Essays
- Builder Essays
- Cerebral Palsy Essays
- Imitation Essays
- Gander Essays
- Prohibition Essays
- Big Data Essays
- Disparity Essays
- Racial Discrimination Essays
- Foot Essays
- Practitioner Essays
We use cookies to improve your experience with our site. Please accept before continuing or read our cookie policy here .
Wait, have you seen our prices?
For enquiries call:
+1-469-442-0620

- Cloud Computing
Top 10 Cloud Computing Research Topics of 2024
Home Blog Cloud Computing Top 10 Cloud Computing Research Topics of 2024
Cloud computing is a fast-growing area in the technical landscape due to its recent developments. If we look ahead to 2024, there are new research topics in cloud computing that are getting more traction among researchers and practitioners. Cloud computing has ranged from new evolutions on security and privacy with the use of AI & ML usage in the Cloud computing for the new cloud-based applications for specific domains or industries. In this article, we will investigate some of the top cloud computing research topics for 2024 and explore what we get most out of it for researchers or cloud practitioners. To master a cloud computing field, we need to check these Cloud Computing online courses .
Why Cloud Computing is Important for Data-driven Business?
The Cloud computing is crucial for data-driven businesses because it provides scalable and cost-effective ways to store and process huge amounts of data. Cloud-based storage and analytical platform helps business to easily access their data whenever required irrespective of where it is located physically. This helps businesses to take good decisions about their products and marketing plans.
Cloud computing could help businesses to improve their security in terms of data, Cloud providers offer various features such as data encryption and access control to their customers so that they can protect the data as well as from unauthorized access.
Few benefits of Cloud computing are listed below:
- Scalability: With Cloud computing we get scalable applications which suits for large scale production systems for Businesses which store and process large sets of data.
- Cost-effectiveness : It is evident that Cloud computing is cost effective solution compared to the traditional on-premises data storage and analytical solutions due to its scaling capacity which leads to saving more IT costs.
- Security : Cloud providers offer various security features which includes data encryption and access control, that can help businesses to protect their data from unauthorized access.
- Reliability : Cloud providers ensure high reliability to their customers based on their SLA which is useful for the data-driven business to operate 24X7.
Top 10 Cloud Computing Research Topics
1. neural network based multi-objective evolutionary algorithm for dynamic workflow scheduling in cloud computing.
Cloud computing research topics are getting wider traction in the Cloud Computing field. These topics in the paper suggest a multi-objective evolutionary algorithm (NN-MOEA) based on neural networks for dynamic workflow scheduling in cloud computing. Due to the dynamic nature of cloud resources and the numerous competing objectives that need to be optimized, scheduling workflows in cloud computing is difficult. The NN-MOEA algorithm utilizes neural networks to optimize multiple objectives, such as planning, cost, and resource utilization. This research focuses on cloud computing and its potential to enhance the efficiency and effectiveness of businesses' cloud-based workflows.
The algorithm predicts workflow completion time using a feedforward neural network based on input and output data sizes and cloud resources. It generates a balanced schedule by taking into account conflicting objectives and projected execution time. It also includes an evolutionary algorithm for future improvement.
The proposed NN-MOEA algorithm has several benefits, such as the capacity to manage dynamic changes in cloud resources and the capacity to simultaneously optimize multiple objectives. The algorithm is also capable of handling a variety of workflows and is easily expandable to include additional goals. The algorithm's use of neural networks to forecast task execution times is a crucial component because it enables the algorithm to generate better schedules and more accurate predictions.
The paper concludes by presenting a novel multi-objective evolutionary algorithm-based neural network-based approach to dynamic workflow scheduling in cloud computing. In terms of optimizing multiple objectives, such as make span and cost, and achieving a better balance between them, these cloud computing dissertation topics on the proposed NN-MOEA algorithm exhibit encouraging results.
Key insights and Research Ideas:
Investigate the use of different neural network architectures for predicting the future positions of optimal solutions. Explore the use of different multi-objective evolutionary algorithms for solving dynamic workflow scheduling problems. Develop a cloud-based workflow scheduling platform that implements the proposed algorithm and makes it available to researchers and practitioners.
2. A systematic literature review on cloud computing security: threats and mitigation strategies
This is one of cloud computing security research topics in the cloud computing paradigm. The authors then provide a systematic literature review of studies that address security threats to cloud computing and mitigation techniques and were published between 2010 and 2020. They list and classify the risks and defense mechanisms covered in the literature, as well as the frequency and distribution of these subjects over time.
The paper suggests the data breaches, Insider threats and DDoS attack are most discussed threats to the security of cloud computing. Identity and access management, encryption, and intrusion detection and prevention systems are the mitigation techniques that are most frequently discussed. Authors depict the future trends of machine learning and artificial intelligence might help cloud computing to mitigate its risks.
The paper offers a thorough overview of security risks and mitigation techniques in cloud computing, and it emphasizes the need for more research and development in this field to address the constantly changing security issues with cloud computing. This research could help businesses to reduce the amount of spam that they receive in their cloud-based email systems.
Explore the use of blockchain technology to improve the security of cloud computing systems. Investigate the use of machine learning and artificial intelligence to detect and prevent cloud computing attacks. Develop new security tools and technologies for cloud computing environments.
3. Spam Identification in Cloud Computing Based on Text Filtering System
A text filtering system is suggested in the paper "Spam Identification in Cloud Computing Based on Text Filtering System" to help identify spam emails in cloud computing environments. Spam emails are a significant issue in cloud computing because they can use up computing resources and jeopardize the system's security.
To detect spam emails, the suggested system combines text filtering methods with machine learning algorithms. The email content is first pre-processed by the system, which eliminates stop words and stems the remaining words. The preprocessed text is then subjected to several filters, including a blacklist filter and a Bayesian filter, to identify spam emails.
In order to categorize emails as spam or non-spam based on their content, the system also employs machine learning algorithms like decision trees and random forests. The authors use a dataset of emails gathered from a cloud computing environment to train and test the system. They then assess its performance using metrics like precision, recall, and F1 score.
The findings demonstrate the effectiveness of the proposed system in detecting spam emails, achieving high precision and recall rates. By contrasting their system with other spam identification systems, the authors also show how accurate and effective it is.
The method presented in the paper for locating spam emails in cloud computing environments has the potential to improve the overall security and performance of cloud computing systems. This is one of the interesting clouds computing current research topics to explore and innovate. This is one of the good Cloud computing research topics to protect the Mail threats.
Create a stronger spam filtering system that can recognize spam emails even when they are made to avoid detection by more common spam filters. examine the application of artificial intelligence and machine learning to the evaluation of spam filtering system accuracy. Create a more effective spam filtering system that can handle a lot of emails quickly and accurately.
4. Blockchain data-based cloud data integrity protection mechanism
The "Blockchain data-based cloud data integrity protection mechanism" paper suggests a method for safeguarding the integrity of cloud data and which is one of the Cloud computing research topics. In order to store and process massive amounts of data, cloud computing has grown in popularity, but issues with data security and integrity still exist. For the proposed mechanism to guarantee the availability and integrity of cloud data, data redundancy and blockchain technology are combined.
A data redundancy layer, a blockchain layer, and a verification and recovery layer make up the mechanism. For availability in the event of server failure, the data redundancy layer replicates the cloud data across multiple cloud servers. The blockchain layer stores the metadata (such as access rights) and hash values of the cloud data and access control information
Using a dataset of cloud data, the authors assess the performance of the suggested mechanism and compare it to other cloud data protection mechanisms. The findings demonstrate that the suggested mechanism offers high levels of data availability and integrity and is superior to other mechanisms in terms of processing speed and storage space.
Overall, the paper offers a promising strategy for using blockchain technology to guarantee the availability and integrity of cloud data. The suggested mechanism may assist in addressing cloud computing's security issues and enhancing the dependability of cloud data processing and storage. This research could help businesses to protect the integrity of their cloud-based data from unauthorized access and manipulation.
Create a data integrity protection system based on blockchain that is capable of detecting and preventing data tampering in cloud computing environments. For enhancing the functionality and scalability of blockchain-based data integrity protection mechanisms, look into the use of various blockchain consensus algorithms. Create a data integrity protection system based on blockchain that is compatible with current cloud computing platforms. Create a safe and private data integrity protection system based on blockchain technology.
5. A survey on internet of things and cloud computing for healthcare
This article suggests how recent tech trends like the Internet of Things (IoT) and cloud computing could transform the healthcare industry. It is one of the Cloud computing research topics. These emerging technologies open exciting possibilities by enabling remote patient monitoring, personalized care, and efficient data management. This topic is one of the IoT and cloud computing research papers which aims to share a wider range of information.
The authors categorize the research into IoT-based systems, cloud-based systems, and integrated systems using both IoT and the cloud. They discussed the pros of real-time data collection, improved care coordination, automated diagnosis and treatment.
However, the authors also acknowledge concerns around data security, privacy, and the need for standardized protocols and platforms. Widespread adoption of these technologies faces challenges in ensuring they are implemented responsibly and ethically. To begin the journey KnowledgeHut’s Cloud Computing online course s are good starter for beginners so that they can cope with Cloud computing with IOT.
Overall, the paper provides a comprehensive overview of this rapidly developing field, highlighting opportunities to revolutionize how healthcare is delivered. New devices, systems and data analytics powered by IoT, and cloud computing could enable more proactive, preventative and affordable care in the future. But careful planning and governance will be crucial to maximize the value of these technologies while mitigating risks to patient safety, trust and autonomy. This research could help businesses to explore the potential of IoT and cloud computing to improve healthcare delivery.
Examine how IoT and cloud computing are affecting patient outcomes in various healthcare settings, including hospitals, clinics, and home care. Analyze how well various IoT devices and cloud computing platforms perform in-the-moment patient data collection, archival, and analysis. assessing the security and privacy risks connected to IoT devices and cloud computing in the healthcare industry and developing mitigation strategies.
6. Targeted influence maximization based on cloud computing over big data in social networks
Big data in cloud computing research papers are having huge visibility in the industry. The paper "Targeted Influence Maximization based on Cloud Computing over Big Data in Social Networks" proposes a targeted influence maximization algorithm to identify the most influential users in a social network. Influence maximization is the process of identifying a group of users in a social network who can have a significant impact or spread information.
A targeted influence maximization algorithm is suggested in the paper "Targeted Influence maximization based on Cloud Computing over Big Data in Social Networks" to find the most influential users in a social network. The process of finding a group of users in a social network who can make a significant impact or spread information is known as influence maximization.
Four steps make up the suggested algorithm: feature extraction, classification, influence maximization, and data preprocessing. The authors gather and preprocess social network data, such as user profiles and interaction data, during the data preprocessing stage. Using machine learning methods like text mining and sentiment analysis, they extract features from the data during the feature extraction stage. Overall, the paper offers a promising strategy for maximizing targeted influence using big data and Cloud computing research topics to look into. The suggested algorithm could assist companies and organizations in pinpointing their marketing or communication strategies to reach the most influential members of a social network.
Key insights and Research Ideas:
Develop a cloud-based targeted influence maximization algorithm that can effectively identify and influence a small number of users in a social network to achieve a desired outcome. Investigate the use of different cloud computing platforms to improve the performance and scalability of cloud-based targeted influence maximization algorithms. Develop a cloud-based targeted influence maximization algorithm that is compatible with existing social network platforms. Design a cloud-based targeted influence maximization algorithm that is secure and privacy-preserving.
7. Security and privacy protection in cloud computing: Discussions and challenges
Cloud computing current research topics are getting traction, this is of such topic which provides an overview of the challenges and discussions surrounding security and privacy protection in cloud computing. The authors highlight the importance of protecting sensitive data in the cloud, with the potential risks and threats to data privacy and security. The article explores various security and privacy issues that arise in cloud computing, including data breaches, insider threats, and regulatory compliance.
The article explores challenges associated with implementing these security measures and highlights the need for effective risk management strategies. Azure Solution Architect Certification course is suitable for a person who needs to work on Azure cloud as an architect who will do system design with keep security in mind.
Final take away of cloud computing thesis paper by an author points out by discussing some of the emerging trends in cloud security and privacy, including the use of artificial intelligence and machine learning to enhance security, and the emergence of new regulatory frameworks designed to protect data in the cloud and is one of the Cloud computing research topics to keep an eye in the security domain.
Develop a more comprehensive security and privacy framework for cloud computing. Explore the options with machine learning and artificial intelligence to enhance the security and privacy of cloud computing. Develop more robust security and privacy mechanisms for cloud computing. Design security and privacy policies for cloud computing that are fair and transparent. Educate cloud users about security and privacy risks and best practices.
8. Intelligent task prediction and computation offloading based on mobile-edge cloud computing
This Cloud Computing thesis paper "Intelligent Task Prediction and Computation Offloading Based on Mobile-Edge Cloud Computing" proposes a task prediction and computation offloading mechanism to improve the performance of mobile applications under the umbrella of cloud computing research ideas.
An algorithm for offloading computations and a task prediction model makes up the two main parts of the suggested mechanism. Based on the mobile application's usage patterns, the task prediction model employs machine learning techniques to forecast its upcoming tasks. This prediction is to decide whether to execute a specific task locally on the mobile device or offload the computation of it to the cloud.
Using a dataset of mobile application usage patterns, the authors assess the performance of the suggested mechanism and compare it to other computation offloading mechanisms. The findings demonstrate that the suggested mechanism performs better in terms of energy usage, response time, and network usage.
The authors also go over the difficulties in putting the suggested mechanism into practice, including the need for real-time task prediction and the trade-off between offloading computation and network usage. Additionally, they outline future research directions for mobile-edge cloud computing applications, including the use of edge caching and the integration of blockchain technology for security and privacy.
Overall, the paper offers a promising strategy for enhancing mobile application performance through mobile-edge cloud computing. The suggested mechanism might improve the user experience for mobile users while lowering the energy consumption and response time of mobile applications. These Cloud computing dissertation topic leads to many innovation ideas.
Develop an accurate task prediction model considering mobile device and cloud dynamics. Explore machine learning and AI for efficient computation offloading. Create a robust framework for diverse tasks and scenarios. Design a secure, privacy-preserving computation offloading mechanism. Assess computation offloading effectiveness in real-world mobile apps.
9. Cloud Computing and Security: The Security Mechanism and Pillars of ERPs on Cloud Technology
Enterprise resource planning (ERP) systems are one of the Cloud computing research topics in particular face security challenges with cloud computing, and the paper "Cloud Computing and Security: The Security Mechanism and Pillars of ERPs on Cloud Technology" discusses these challenges and suggests a security mechanism and pillars for protecting ERP systems on cloud technology.
The authors begin by going over the benefits of ERP systems and cloud computing as well as the security issues with cloud computing, like data breaches and insider threats. They then go on to present a security framework for cloud-based ERP systems that is built around four pillars: access control, data encryption, data backup and recovery, and security monitoring. The access control pillar restricts user access, while the data encryption pillar secures sensitive data. Data backup and recovery involve backing up lost or failed data. Security monitoring continuously monitors the ERP system for threats. The authors also discuss interoperability challenges and the need for standardization in securing ERP systems on the cloud. They propose future research directions, such as applying machine learning and artificial intelligence to security analytics.
Overall, the paper outlines a thorough strategy for safeguarding ERP systems using cloud computing and emphasizes the significance of addressing security issues related to this technology. Organizations can protect their ERP systems and make sure the Security as well as privacy of their data by implementing these security pillars and mechanisms.
Investigate the application of blockchain technology to enhance the security of cloud-based ERP systems. Look into the use of machine learning and artificial intelligence to identify and stop security threats in cloud-based ERP systems. Create fresh security measures that are intended only for cloud-based ERP systems. By more effectively managing access control and data encryption, cloud-based ERP systems can be made more secure. Inform ERP users about the security dangers that come with cloud-based ERP systems and how to avoid them.
10. Optimized data storage algorithm of IoT based on cloud computing in distributed system
The article proposes an optimized data storage algorithm for Internet of Things (IoT) devices which runs on cloud computing in a distributed system. In IoT apps, which normally generate huge amounts of data by various devices, the algorithm tries to increase the data storage and faster retrials of the same.
The algorithm proposed includes three main components: Data Processing, Data Storage, and Data Retrieval. The Data Processing module preprocesses IoT device data by filtering or compressing it. The Data Storage module distributes the preprocessed data across cloud servers using partitioning and stores it in a distributed database. The Data Retrieval module efficiently retrieves stored data in response to user queries, minimizing data transmission and enhancing query efficiency. The authors evaluated the algorithm's performance using an IoT dataset and compared it to other storage and retrieval algorithms. Results show that the proposed algorithm surpasses others in terms of storage effectiveness, query response time, and network usage.
They suggest future directions such as leveraging edge computing and blockchain technology for optimizing data storage and retrieval in IoT applications. In conclusion, the paper introduces a promising method to improve data archival and retrieval in distributed cloud based IoT applications, enhancing the effectiveness and scalability of IoT applications.
Create a data storage algorithm capable of storing and managing large amounts of IoT data efficiently. Examine the use of cloud computing to improve the performance and scalability of data storage algorithms for IoT. Create a secure and privacy-preserving data storage algorithm. Assess the performance and effectiveness of data storage algorithms for IoT in real-world applications.
How to Write a Perfect Research Paper?
- Choose a topic: Select the topic which is interesting to you so that you can share things with the viewer seamlessly with good content.
- Do your research: Read books, articles, and websites on your topic. Take notes and gather evidence to support your arguments.
- Write an outline: This will help you organize your thoughts and make sure your paper flows smoothly.
- Start your paper: Start with an introduction that grabs the reader's attention. Then, state your thesis statement and support it with evidence from your research. Finally, write a conclusion that summarizes your main points.
- Edit and proofread your paper. Make sure you check the grammatical errors and spelling mistakes.
Cloud computing is a rapidly evolving area with more interesting research topics being getting traction by researchers and practitioners. Cloud providers have their research to make sure their customer data is secured and take care of their security which includes encryption algorithms, improved access control and mitigating DDoS – Deniel of Service attack etc.,
With the improvements in AI & ML, a few features developed to improve the performance, efficiency, and security of cloud computing systems. Some of the research topics in this area include developing new algorithms for resource allocation, optimizing cloud workflows, and detecting and mitigating cyberattacks.
Cloud computing is being used in industries such as healthcare, finance, and manufacturing. Some of the research topics in this area include developing new cloud-based medical imaging applications, building cloud-based financial trading platforms, and designing cloud-based manufacturing systems.
Frequently Asked Questions (FAQs)
Data security and privacy problems, vendor lock-in, complex cloud management, a lack of standardization, and the risk of service provider disruptions are all current issues in cloud computing. Because data is housed on third-party servers, data security and privacy are key considerations. Vendor lock-in makes transferring providers harder and increases reliance on a single one. Managing many cloud services complicates things. Lack of standardization causes interoperability problems and restricts workload mobility between providers.
Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS) are the cloud computing scenarios where industries focusing right now.
The six major components of cloud infrastructure are compute, storage, networking, security, management and monitoring, and database. These components enable cloud-based processing and execution, data storage and retrieval, communication between components, security measures, management and monitoring of the infrastructure, and database services.

Vinoth Kumar P
Vinoth Kumar P is a Cloud DevOps Engineer at Amadeus Labs. He has over 7 years of experience in the IT industry, and is specialized in DevOps, GitOps, DevSecOps, MLOps, Chaos Engineering, Cloud and Cloud Native landscapes. He has published articles and blogs on recent tech trends and best practices on GitHub, Medium, and LinkedIn, and has delivered a DevSecOps 101 talk to Developers community , GitOps with Argo CD Webinar for DevOps Community. He has helped multiple enterprises with their cloud migration, cloud native design, CICD pipeline setup, and containerization journey.
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Cloud Computing Batches & Dates

COMMENTS
Assistant Professor, Ajman University, UAE. Doi: 10.36941/ajis-2020-0008. Abstract. This study is a literature review on cloud computing cloud computing trends as on e the fastest growing ...
This paper presents a meta-analysis of cloud computing research in information systems with the aim of taking stock of literature and their associated research frameworks, research methodology, geographical distribution, level of analysis as well as trends of these studies over the period of 7 years. ... Cloud computing research started to gain ...
Unlike most public serverless computing platforms that primary use scale-per-request autoscaling such as AWS Lambda, Google Cloud Functions, Azure Functions, and IBM Cloud Functions, Knative and consequently Google Cloud Run allow several requests to enter the same func-tion instance at the same time. The number of concurrent
The paper also gives a concise description of Cloud Computing concepts and technologies. It starts with a brief history about cloud computing, tracing its roots. Then, architectural models of cloud services are described, and the most relevant products for Cloud Computing are briefly discussed along with a comprehensive literature review.
The paper further compares and reviews different layout model for the discovery of services, selection of services and composition of services in Cloud computing. Recent research trends in service composition are identified and then research about microservices are evaluated and shown in the form of table and graphs. Download Full-text.
The Journal of Cloud Computing, Advances, Systems and Applications (JoCCASA) has been launched to offer a high quality journal geared entirely towards the research that will offer up future generations of Clouds. The journal publishes research that addresses the entire Cloud stack, and as relates Clouds to wider paradigms and topics.
Cloud computing has taken its place all over the IT industries. It is an on-demand internet-based computing service that provides the maximum result with minimum resources cloud computing provides a service that does not require any physical close to the computer hardware. Cloud Computing is a product of grid, distributed, parallel, and ubiquitous computing. This paper introduces the concepts ...
Huimin Han, Harold Neira-Molina, Asad Khan, Meie Fang, Haitham A. Mahmoud, Emad Mahrous, Bilal Ahmed and Yazeed Yasin Ghadi. Journal of Cloud Computing 2024 13 :77. Correction Published on: 27 March 2024. The original article was published in Journal of Cloud Computing 2024 13 :20. Full Text.
The emergence of the Web in 1990 gave rise to cloud computing; a disruptive innovation in the bird's-eye view of information technology. Cloud computing essentially sidesteps the need for capital investments in hardware and expensive information technology, yet has many hurdles to overcome. The purpose of this review is to identify the most discussed topics and relevant theories, while also ...
This paper is the first systematic review of peer-reviewed academic research published in this field, and aims to provide an overview of the swiftly developing advances in the technical foundations of cloud computing and their research efforts. Structured along the technical aspects on the cloud agenda, we discuss lessons from related ...
Profile Information. Communications Preferences. Profession and Education. Technical Interests. Need Help? US & Canada:+1 800 678 4333. Worldwide: +1 732 981 0060. Contact & Support. About IEEE Xplore.
Resource Management in a Hybrid Cloud Infrastructure. In this paper, a resource management technique is proposed to handle the request of Virtual Machines (VM's) as per the need of users, consisting of resources (mips, vm image size, network bandwidth, number of cpu's) containing cloudlets... more. Download.
cellular networking, as well as the open research areas to gain the maximum value from the combination of telecommunication and cloud computing.[2] This paper's comparative results show that the features of each cloud storage system play a significant role in the decision-making process when switching to cloud services.[3] ...
A principal goal of this paper is to identify privacy and confidentiality issue that may be of interest and concern to cloud computing participants and users [11]. Thus this paper explores to elicit possible issues and regulations in the area of privacy that affect the implementation of Cloud Computing Technologies.
Abstract. This paper discusses cloud computing based on Enterprise Resource Planning (ERP). The cloud computing processing system has become one of the fastest growing areas in the field of Information Technology. The prime purpose of cloud computing is to share the available resources so that economies of scale can be achieved rather than ...
Keywords: Cloud Computing, Cloud security, Distributed Computing, Framework 1. INTRODUCTION Cloud computing is an appropriate design which concentrates server assets on a versatile stage in order to give on request figuring assets and administrations. Cloud Service Providers (CSP's) offer cloud stages for their clients to utilize and make their
4. Blockchain data-based cloud data integrity protection mechanism. The "Blockchain data-based cloud data integrity protection mechanism" paper suggests a method for safeguarding the integrity of cloud data and which is one of the Cloud computing research topics. In order to store and process massive amounts of data, cloud computing has grown ...