- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture

Which Protocol Is Used to Automatically Assign IP Addresses to Hosts?
- What is IPv6 Intra Site Automatic Tunnel Addressing Protocol (ISATAP)?
- How DHCP server dynamically assigns IP address to a host?
- What is APIPA (Automatic Private IP Addressing)?
- Which Command is Used to View the IP Address and Default Gateway of a Computer?
- What Happens When Two Hosts Have the Same IP Address?
- How is a Private IP Address Assigned?
- Who Assigns an IP Address to the Computer?
- What is "network ID" and "host ID" in IP Addresses?
- How to Find Network IP Address of Computer Using Computer Name?
- How does a computer get its MAC and IP addresses?
- Program to find Class, Broadcast and Network addresses
- How Address Resolution Protocol (ARP) works?
- What is My Internet Protocol (IP) Address?
- How to determine the user IP address using node.js ?
- GFact | How to know the IP address(es) of a URL/website?
- IP Rover - OSINT tool to get information of any IP address
- Find All Live Hosts IP Addresses Connected on Network in Linux
- How to Manipulate IP Addresses in Python using ipaddress Module?
- What is IPv6 Stateless Address Autoconfiguration ?
Answer : The Dynamic Host Configuration Protocol (DHCP) is used to automatically assign IP addresses to hosts.
Purpose of dhcp.
DHCP is designed to reduce the administrative burden and complexity of manually configuring IP addresses for networked devices.
How DHCP Works
- A device connects to the network and broadcasts a DHCP discovery message.
- A DHCP server receives the discovery message and responds with an offer message that includes an IP address and other network configuration information, such as DNS server addresses and the subnet mask.
- The device accepts the offer, and the server allocates the IP address to the device, usually for a limited lease time.
Benefits of DHCP
- Automates the IP address configuration process, ensuring devices can communicate on the network without manual setup.
- Helps prevent IP address conflicts by managing the pool of addresses.
DHCP plays a critical role in modern networks by dynamically assigning IP addresses to devices, simplifying network management, and ensuring efficient use of IP addresses.
Please Login to comment...
Similar reads.
- Computer-Networks-MAQ
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
How-To Geek
What is dhcp (dynamic host configuration protocol).
Ever wonder how your devices get an IP automatically?
Quick Links
Dhcp can handle ip assignments, dhcp controls the range of ip addresses, dynamically assigned addresses are temporary, static ip addresses are necessary for some devices, key takeaways.
- DHCP automates the process of assigning IP addresses to devices connecting to a network, making it easier to connect multiple devices.
- DHCP allows you to control the range of IP addresses available for use, ensuring you can limit the number of devices connected to your network.
- While DHCP assigns IP addresses temporarily, static IP addresses are necessary for certain devices (e.g. servers) to maintain consistent connectivity and configuration.
The Dynamic Host Configuration Protocol (DHCP) is integral to networks and controls what IP addresses devices receive so they can communicate with the internet. Usually, IP assignment is automated, but if you need static IPs, familiarity with DHCP is essential.
Every device that connects to a network needs an IP address . In the early days of networking, users manually assigned themselves an IP address, but that's a cumbersome task, especially for places with many devices, such as a corporate office. DHCP, in part, automates this process, which makes connecting devices to the network far easier. DHCP servers or routers handle this process based on a set of defined rules. Most routers are set to use a 192.168.0.x range, for instance, so you'll commonly see IP addresses like this in home networks.
The process is pretty straight forward. When a client (a computer, IOT device , tablet, cell phone, etc.) connects to the network, it sends out a signal (called DHCPDISCOVER) to the DHCP server (or router). The server responds with all the rules and settings for the network and an IP address for use (a DHCPOFFER). The client acknowledges the information and asks permission to use the assigned address (a DHCPREQUEST message). Finally, the DHCP server acknowledges the request, and the client is free to connect to the network.
You can configure DHCP to control the range of IP addresses available for use. If you state that range as starting at 192.168.0.1 and the end as 192.168.0.100, then all available addresses will fall somewhere within that range. You'll never see a device assigned to 192.168.0.101. Also, bear in mind that the start IP (192.168.0.1 in this example) is reserved for the router. Some routers only list a starting address and then include an option for a maximum number of users (which determines the end address).
The upside to this is you can control how many devices connect to your network simultaneously (no more than 100 in this example). But the downside is if you set the range too small you can unintentionally prevent connection of new devices. To allow for a lower range of IP addresses, DHCP servers only lease out IP addresses to devices.
When a DHCP server assigns an IP Address, it does so under a lease system. The machine retains this IP address for a set number of days, after which it can try to renew the IP address. If no renewal signal is sent (such as a decommissioned machine), then the DHCP server reclaims the IP address to assign to another device. When the renewal signal is detected, the device retains its IP address for another set of days. This is why your IP address may appear to change from time to time if you use the ipconfig option often.
It's possible for two devices to end up with the same IP, such as a virtual machine (VM) that spends most of its time offline. The VM won't be able to send the renew signal, so its IP address will be handed out to another machine. When the VM is brought back up, it still has a record of the old IP address (especially if restored from a snapshot), but it won't be able to use that IP address since it is taken. Without that permission, it can't connect to the network until a new IP is assigned. But using dynamic IP addresses should prevent this type of scenario.
If you have a network connected printer or media server (such as a NAS unit Plex Server, or game server), it would be inconvenient for them to have their IP addresses changed. Sometimes hosted services require special configuration to function correctly. For example, a Minecraft server requires that port 25565 is forwarded , and you may have software pointing to your NAS's local IP. If the local IP of the device changes, then any rules (like port forwards) applied to it won't work anymore.
While renewal of the lease can prevent this, it's still possible for the IP address to change. If your router is restarted, due to a power outage or because you're trying to solve a pesky problem , then all Dynamically generated IP addresses may be reassigned. For those scenarios, manually assigning a Static IP address will solve the problem.
The exact process for this varies, especially as router web interfaces can change from device to device even when made by the same manufacturer. On some routers, like the Eero Mesh Router kit , this may be referred to by another term, such as IP reservation. But a static IP address still needs to conform to any range rules, if they exist. Using a current IP address as the basis for a static IP is usually the easiest thing to do. Depending on the device and its Operating System, it may be possible to set a static IP at the device end instead of through the router or DHCP server. This may be necessary if the router itself doesn't support Static IP.
Dynamic Host Configuration Protocol (DHCP)
Last Edited
Dynamic Host Configuration Protocol (DHCP) is a network protocol used to dynamically assign IP addresses and other network settings to devices on a local network. This comprehensive article aims to demystify DHCP, delving into its core components, mechanisms, and real-world applications to equip computer science students and professionals with essential knowledge.
In this article:
Part I: Introduction to Concepts Related to DHCP
- Introduction to Network Protocols
- The Need for DHCP in Modern Networks
- How DHCP Fits into the OSI Model
- IP Address, Subnet Mask, and Gateway
- DHCP vs. Static IP Addresses
- Components of DHCP
- Lease Time and Renewal
Part II: How DHCP Works – A Comprehensive Guide
- The Four-Step DHCP Process
- DHCP Options
- DHCP Discover Mechanism
- DHCP Offer Mechanism
- DHCP Request and Acknowledgment
- DHCP Renewal Process
- Failover and Redundancy
- Security Concerns and Mitigations
Part III: Practical Examples and Use-Cases
- Configuring a DHCP Server on Windows
- Configuring a DHCP Server on Linux
- DHCP Troubleshooting
- Use-Case-DHCP-in-a-Home-Network
- Use-Case: DHCP in Enterprise Networks
- Advanced DHCP Features
Part IV: Extra Content
- Video Explainer: How Your PC Gets Its IP Address?
- Further Reading
1. Introduction to Network Protocols
Network protocols are a set of rules and conventions that govern the interaction between computers and other devices in a network. Think of them as the “language” devices speak to transmit data efficiently and securely. They dictate how information is packaged, sent, received, and interpreted. These rules are essential for maintaining order, ensuring that data gets to its intended destination without errors, and enabling disparate devices to communicate seamlessly.
In today’s interconnected world, network protocols are the backbone of any data exchange over the Internet, whether it’s a simple email or a complex cloud-based application. Without standardized protocols, we would face a Tower of Babel in networking, making it near-impossible for different systems to understand each other. From HTTP for web browsing to SMTP for email, protocols are indispensable in ensuring smooth data transfer and, by extension, the functioning of modern society.
2. The Need for DHCP in Modern Networks
In the early days of networking, IP addresses were often assigned manually in a process known as static allocation. Administrators had to individually configure each device, a cumbersome and error-prone task. Imagine having to manually assign addresses for each device in a large organization; not only is this labor-intensive, but it also increases the risk of misconfiguration and IP conflicts. Furthermore, tracking which IP addresses have been allocated and which are available becomes a logistical nightmare as networks grow.
Enter DHCP, or Dynamic Host Configuration Protocol. DHCP automates this IP assignment, thus simplifying network management exponentially. When a device joins a network, the DHCP server automatically assigns it an IP address from a pool of available addresses, along with other network configurations like the subnet mask and default gateway. This is not just convenient; it’s also more efficient, reducing the chances of IP conflicts and freeing up valuable administrative time for other tasks.
The DHCP server also ‘leases’ these IP addresses for a set period, reclaiming them when they’re not in use. This dynamic nature makes DHCP highly scalable, allowing for easy addition or removal of devices without manual reconfiguration. In essence, DHCP not only streamlines network management but also paves the way for network expansion and adaptability, characteristics intrinsic to modern networks.
3. How DHCP Fits into the OSI Model
Understanding where DHCP stands in the OSI (Open Systems Interconnection) model provides valuable context for its role in networking. The OSI model serves as a framework for understanding how different networking protocols interact and operate. It is divided into seven layers, starting from the Physical layer at the bottom to the Application layer at the top.
DHCP primarily operates at the Application layer, the seventh layer of the OSI model. However, its functionality has implications that cascade down to the Network layer, where IP addresses operate. While the Application layer is responsible for network services to end-user applications, the Network layer deals with routing and forwarding packets across the network.
The importance of DHCP operating at the Application layer lies in its ability to facilitate higher-level application tasks while influencing lower-layer functions, like IP address allocation. By interacting with both user applications and the core network infrastructure, DHCP serves as a bridge, uniting various elements of network management into a cohesive system. This multi-layer operation is crucial for the protocol’s versatility and its broad range of features beyond just IP address allocation.
4. IP Address, Subnet Mask, and Gateway
Understanding DHCP inevitably involves a grasp of three key components: IP Address, Subnet Mask, and Gateway . Let’s delve into each:
- IP Address: This is the unique identifier for each device on a network. Think of it like a home address but for your computer or smartphone. IP addresses enable devices to locate each other and communicate effectively.
- Subnet Mask: A subnet mask works alongside an IP address to identify which part of the address designates the network and which part designates the device. By separating the network ID from the host ID , subnet masks enable efficient routing within a local network and facilitate communication between multiple subnets within a larger network.
- Gateway: The gateway serves as the intermediary device that connects your local network to external networks, most commonly the Internet . When a device needs to communicate with another network, it sends the data to the gateway, which then routes it to the appropriate destination.
Together, these components play vital roles in a network, forming the backbone of how devices communicate and interact. DHCP automates the configuration of these settings, allowing devices to connect to a network and communicate with each other effortlessly. By dynamically assigning these configurations, DHCP ensures optimal network performance and simplifies the task of network management.
5. DHCP vs. Static IP Addresses
When it comes to IP address allocation, there are essentially two methodologies—Dynamic Host Configuration Protocol (DHCP) and Static IP addresses. Both have their merits, but they serve different needs and scenarios.
- Dynamic Allocation: DHCP assigns IP addresses dynamically, meaning devices could have a different IP address each time they connect to the network.
- Efficiency: DHCP is easier to manage, especially in large networks where devices frequently join or leave.
- Scalability: Ideal for environments where devices are constantly changing, as new addresses can be automatically allocated and old ones recycled.
- Risk Mitigation: Reduced risk of IP address conflicts and errors as everything is managed by the DHCP server.
Static IP Addresses:
- Permanent Allocation: A device keeps the same IP address until manually changed, providing a predictable and consistent identifier.
- Resource Intensive: Requires manual configuration and meticulous record-keeping, making it labor-intensive.
- Precision Control: Suited for network devices that need a fixed IP for specific tasks or permissions.
- Stability: Once set, there’s no risk of the address changing, which is vital for some server tasks and network configurations.
Comparative Takeaways:
- DHCP is excellent for most standard network configurations due to its automatic management features.
- Static IPs are preferable for devices that require constant, unchanging access, such as servers or dedicated workstations.
Understanding the strengths and limitations of DHCP and static IPs enables network administrators to make educated decisions on how to best allocate network resources.
6. Components of DHCP
DHCP operates through a client-server model, involving several key components that work in unison to enable dynamic IP address allocation. Understanding these components is crucial for anyone wanting to grasp the intricacies of DHCP.
- DHCP Server: This is the heart of the DHCP operation. The server stores the range of IP addresses to be allocated, known as the address pool, and other network settings. When a client requests an IP address, the server selects one from its pool and offers it to the client.
- DHCP Client: Any device that connects to a DHCP-enabled network acts as a DHCP client. The client requests network settings from the DHCP server, accepts the offer, and configures itself based on the received information.
- DHCP Relay Agent: In larger, segmented networks, a DHCP relay agent helps transmit messages between DHCP clients and servers that don’t reside on the same physical subnet. The relay agent forwards client requests to the server and returns the server’s responses back to the client.
Each of these components plays a vital role in the DHCP ecosystem. Together, they automate the network configuration process, making it easier, faster, and more efficient for both administrators and end-users.
7. Lease Time and Renewal
Lease time is a crucial aspect of DHCP that often goes overlooked, yet it is fundamental to understanding how DHCP maintains efficient network management. In simple terms, lease time is the duration for which an IP address is “rented out” to a DHCP client by the DHCP server. It’s a timer that starts ticking the moment the IP address is assigned. Lease times can vary, ranging from as short as a few minutes to as long as several days, depending on the network’s requirements and the administrator’s preferences.
Why is Lease Time Important?
- Resource Management: Limited IP addresses can be effectively reused, ensuring optimal resource utilization.
- Dynamic Adaptation: It allows for more effortless network reconfiguration, as IP addresses are not permanently tied to clients.
- Network Integrity: Lease time minimizes the risk of IP address conflicts since addresses are periodically returned and reassigned.
The Renewal Process
IP address renewal is the mechanism by which an active DHCP lease is extended. Here’s how it typically works:
- Halfway Through: Once the lease time reaches its halfway point, the DHCP client initiates a renewal request, commonly sent directly to the DHCP server that initially granted the lease.
- Server Response: Upon receiving the renewal request, the DHCP server may extend the lease, allowing the client to keep its current IP address for another lease period.
- Failure to Renew: If the client fails to renew its lease, either because the server is down or the client has moved to a different network, the DHCP client will attempt to renew its lease with any available DHCP server when 87.5% of the lease time has expired.
- Lease Expiry: If the client still fails to renew the lease after reaching the end of the allocated lease time, it must discontinue using the IP address and initiate the DHCP process anew to obtain a new address.
Understanding lease time and the renewal process helps to illustrate the self-sustaining and automated nature of DHCP, features that make it an invaluable tool in modern network management.
8. The Four-Step DHCP Process
One of the most fundamental aspects of the Dynamic Host Configuration Protocol is the Four-Step DHCP Process, commonly known by its acronym, DORA, which stands for Discovery, Offer, Request, and Acknowledgment. Understanding these four stages is crucial for anyone delving into DHCP, whether you’re a student, an IT professional, or a network administrator.
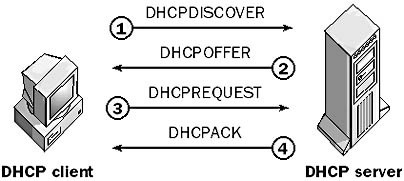
- Discovery: The process starts with the DHCP client sending out a broadcast message—known as a DHCPDISCOVER message—to identify any available DHCP servers on the network.
- Offer: Upon receiving the DHCPDISCOVER message, the DHCP server sends back a DHCPOFFER message, offering an IP address and additional network settings to the client. If multiple servers send offers, the client generally accepts the first one it receives.
- Request: The client responds by broadcasting a DHCPREQUEST message to indicate its acceptance of the offered IP address. This step serves as a confirmation and informs other DHCP servers that their offers are declined.
- Acknowledgment: Finally, the DHCP server sends a DHCPACK message, confirming that the IP address has been officially allocated to the client. The server also provides additional network configuration details, setting the stage for successful network communication.
This DORA process automates IP address allocation, making network configuration both efficient and error-free.
9. DHCP Options
DHCP is not just about IP address allocation; it also provides a variety of options that allow for more complex and customized network configurations. These “ DHCP Options ” are a set of pre-defined, standardized settings that the DHCP server can send to the client along with the IP address.
Some commonly used DHCP options include:
- Option 3: Router (Default Gateway)
- Option 6: DNS Servers
- Option 15: Domain Name
- Option 42: NTP Servers
Why Are DHCP Options Important?
- Customization: DHCP options enable network administrators to offer specific configurations tailored to meet the individual needs of each client or network.
- Simplified Management: By including various settings in the DHCP offer, administrators can control multiple aspects of network behavior without requiring manual configuration on each client.
- Network Services: Some DHCP options can point clients to additional network services, such as VoIP servers or proxy configurations, thereby extending the protocol’s capabilities beyond mere IP address assignment.
Understanding DHCP options is essential for anyone looking to unlock the full potential of DHCP in complex, multi-faceted network environments.
» Read next: How to implement DHCP Option 82 for security?
10. Dynamic Host Configuration Protocol Discover Mechanism
The DHCP Discover mechanism is the initial stage in the four-step DHCP process known as DORA (Discovery, Offer, Request, Acknowledgment). In this phase, a client that joins a network and needs an IP address to participate in it actively seeks out a DHCP server. Here’s how it works:
Steps of the Discover Mechanism:
- Initialization: When a DHCP client connects to a network, it broadcasts a DHCPDISCOVER message. This is a general broadcast, as the client is unaware of any DHCP servers on the network.
- Packet Details: The DHCPDISCOVER packet usually contains the client’s MAC address and may contain the desired IP address, although the latter is optional.
- Broadcast Domain: The message is broadcast across the local network domain. If the network has multiple subnets, a DHCP Relay Agent can forward the DHCPDISCOVER message to other subnets.
- Waiting for Response: After broadcasting the DHCPDISCOVER message, the client waits for a DHCPOFFER message from a DHCP server.
Significance:
- Network Efficiency: The DHCP Discover mechanism ensures that IP addresses are only assigned to clients that require them, optimizing network resource utilization.
- Automated Configuration: This automated process negates the need for manual IP address configuration, simplifying the network setup process.
11. DHCP Offer Mechanism
Following the Discovery phase, the next critical step is the DHCP Offer mechanism. This is where the DHCP server offers an IP address to the client based on the range of available addresses in its pool. Let’s break it down:
Steps of the Offer Mechanism:
- Receiving Discovery: The DHCP server receives the DHCPDISCOVER broadcast message from the client.
- IP Address Allocation: The server selects an available IP address from its pool and temporarily reserves it for the client.
- Forming the Offer: The server then constructs a DHCPOFFER message containing the selected IP address and additional network settings.
- Sending the Offer: The server broadcasts the DHCPOFFER message back to the client. If multiple DHCP servers are available, the client may receive multiple offers but generally accepts the first one it gets.
- Automated Management: The DHCP Offer mechanism allows the server to manage its IP address pool efficiently, reducing the risk of conflicts and duplication.
- Flexible Configuration: The server can also include other network settings, like the default gateway and DNS server addresses, streamlining the client’s network setup.
By understanding these individual mechanisms within the broader DORA process, you’ll gain a richer insight into how DHCP works and why it’s an invaluable tool for modern networks.
12. DHCP Request and Acknowledgment
After receiving one or more offers from DHCP servers in the network, the client enters the Request and Acknowledgment phases to complete the DORA process.
Request Phase:
- Accepting the Offer: The client chooses one offer (generally the first it receives) and broadcasts a DHCPREQUEST message to notify all servers about the accepted offer.
- Multiple Offers: In case of multiple offers, this broadcast ensures that only the chosen server finalizes the IP assignment while informing the other servers to withdraw their offers.
- Final Confirmation: The DHCPREQUEST message serves as the client’s formal acceptance and is also the final check to ensure that the IP address is still valid and has not been allocated elsewhere in the interim.
Acknowledgment Phase:
- Finalizing Assignment: The chosen DHCP server responds with a DHCPACK message, confirming the assignment and providing additional network configuration information.
- Completing the Handshake: Upon receiving the DHCPACK, the client completes its network configuration and becomes an active participant in the network.
- Nack Response: If the server finds that the IP is no longer available or if the request is invalid, it sends a DHCPNACK, forcing the client to restart the DORA process.
By clearly understanding the Request and Acknowledgment steps, you complete the full circle of how DHCP dynamically manages IP addresses within a network.
13. DHCP Renewal Process
Lease renewal is an integral part of DHCP that ensures IP addresses are efficiently managed and allocated over time. Here’s how it operates:
- T1 Timer: When the lease time reaches its halfway point (T1 timer), the client attempts to renew the lease by sending a DHCPREQUEST directly to the server that initially granted the IP address.
- Server Response: If the server approves the renewal, it sends back a DHCPACK with a new lease time, effectively renewing the client’s lease.
- T2 Timer: If the T1 timer expires and the lease is not renewed, a second timer (T2) starts, during which the client broadcasts a DHCPREQUEST to any available server for a new lease.
- Lease Expiration: If the client fails to renew its lease before it fully expires, it must release its current IP address and start the DORA process anew to acquire a new IP address.
The renewal process underscores DHCP’s dynamic nature, allowing for ongoing network changes while maintaining stable operations.
14. Failover and Redundancy
In a production environment, relying on a single DHCP server is a recipe for disaster. Network uptime is crucial, and a single point of failure is unacceptable. Hence, DHCP servers are often configured to be redundant to avoid failure.
DHCP Failover:
- Active-Active: In an active-active configuration, two or more DHCP servers share responsibility for a subnet. Each server can respond to any client request, offering high availability and load balancing.
- Active-Passive: One server actively handles DHCP requests while the other is on standby, ready to take over if the active server fails.
Load Balancing:
- Multiple Dynamic Host Configuration Protocol servers can be configured to share the load of client requests, enhancing performance and reliability.
- High Availability: Redundant DHCP servers ensure there’s no downtime in IP address allocation, which is critical for maintaining network operations.
- Scalability: As the network grows, additional DHCP servers can be added seamlessly to share the load.
By implementing failover and redundancy, network administrators can ensure that DHCP services are always available, even when individual servers fail.
15. Security Concerns and Mitigations
Like any network protocol, Dynamic Host Configuration Protocol is not without its security risks. However, understanding these risks is the first step in mitigating them effectively.
- Rogue DHCP Servers: Unauthorized DHCP servers can be set up to provide incorrect configurations, leading to potential security breaches.
- DHCP Snooping Attacks: Attackers can snoop on DHCP traffic to gather information like IP addresses and MAC addresses for malicious purposes.
Mitigations:
- DHCP Snooping: Network switches can be configured to filter and control DHCP traffic, permitting only authorized servers to operate.
- IP-MAC Binding: Binding specific IP addresses to known MAC addresses can prevent unauthorized devices from obtaining network access.
- Network Segmentation: Limiting DHCP traffic to specific VLANs can contain the potential impact of rogue DHCP servers.
- Regular Audits: Consistent monitoring and logging can help in the early detection of unauthorized DHCP activity, allowing for immediate corrective action.
Understanding and addressing these security concerns are essential for maintaining the integrity and reliability of Dynamic Host Configuration Protocol operations within a network.
16. Configuring a DHCP Server on Windows
For those who prefer learning by doing, this comprehensive guide will walk you through the process of setting up a DHCP server on a Windows machine. Whether you’re setting this up in a lab for educational purposes or deploying it in a production environment, the following steps should provide you with a smooth experience.
Prerequisites:
- Windows Server OS (2012, 2016, 2019, etc.)
- Administrative access to the server
- Basic understanding of network configurations
Step 1: Open Server Manager
- Log in to your Windows Server machine.
- Open Server Manager by clicking its icon on the taskbar, or by searching for it in the Start menu.
Step 2: Add the DHCP Role
- In the Server Manager Dashboard, click on “Add roles and features.”
- Navigate through the wizard until you reach the “Roles” tab.
- Scroll down and check the “DHCP Server” role.
Step 3: Confirm Installation
- Click “Next” until you reach the “Confirm installation selections” screen.
- Confirm your settings and click “Install.”
- Wait for the installation process to complete.
Step 4: Post-Installation Configuration
- Once installed, go back to the Server Manager Dashboard.
- Click the yellow triangle on the top right to open the Notifications pane.
- Click “Complete DHCP configuration” and follow the on-screen instructions.
Step 5: Configure DHCP Scope
- Open the DHCP management console by clicking on “Tools” in the Server Manager, then select “DHCP.”
- In the DHCP console, right-click on your server and choose “New Scope.”
- Follow the New Scope Wizard, specifying the range of IP addresses to be allocated, lease durations, and other settings as needed.
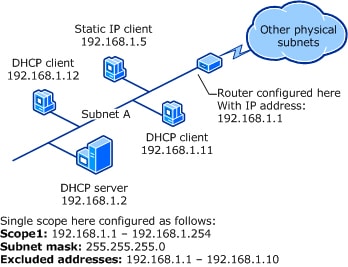
Step 6: Authorize the DHCP Server
- In the DHCP console, right-click on your server and choose “Authorize.”
- Wait a few moments for the server to be authorized. You should see a green checkmark appear next to your server when the process is complete.
Step 7: Verify the Configuration
- Use a DHCP client to request an IP address from your new DHCP server.
- Check the DHCP leasing table in the DHCP console to confirm that the IP address has been successfully allocated.
Step 8: Advanced Settings (Optional)
- Reservations: You can reserve specific IP addresses for certain devices using their MAC addresses.
- Options: You can configure global or scope-specific options such as DNS servers , NTP servers , etc.
Troubleshooting:
- If the server isn’t authorizing, ensure that it is connected to the network and that you are using an administrative account.
- Check Windows Firewall settings to ensure that DHCP traffic is allowed.
By following these steps, you should have a functional DHCP server up and running on your Windows machine. The practical knowledge gained through this hands-on guide will deepen your understanding of DHCP and equip you for real-world applications.
17. Configuring a DHCP Server on Linux
For those running Linux environments, configuring a DHCP server can be a cost-effective and highly customizable solution. This comprehensive guide aims to walk you through the setup process, whether you’re doing this for educational purposes or implementing it in a live setting.
- A machine running a Linux distribution (Ubuntu, CentOS, etc.)
- Root or sudo access
- Basic familiarity with Linux terminal commands
- A text editor like Vim, Nano, or any of your choosing
Step 1: Update Your System
- Open your terminal.
- Update your package lists and packages:
Step 2: Install the DHCP Server Package
- Install the DHCP server package:

Step 3: Configure Interface
- Identify the network interface you wish to serve DHCP requests on:
- Edit the DHCP server default settings:
Add your interface to the INTERFACESv4 or INTERFACESv6 line.
Step 4: Configure DHCP Settings
- Backup the original configuration file:
- Open the configuration file for editing:
- Add your DHCP settings. For example:
Step 5: Start the DHCP Server
- Start and enable the DHCP service:
Step 6: Firewall Configuration
- Allow DHCP traffic through the firewall:
Step 7: Testing and Verification
- Test the DHCP server by connecting a DHCP client to the network.
- Verify that the client receives an IP address from the range you specified.
- Run sudo systemctl status isc-dhcp-server to check the service status.
- Examine logs for issues: cat /var/log/syslog | grep dhcp
- Static IP Assignments: You can assign static IPs by specifying host blocks in dhcpd.conf .
- Option Modification: You can customize options like DNS and NTP directly in dhcpd.conf .
By completing these steps, you should have a fully functional DHCP server running on your Linux machine. This hands-on guide aims to give you both the theoretical and practical tools needed to manage DHCP effectively in Linux environments.
18. DHCP Troubleshooting
Troubleshooting is an essential skill for anyone involved in network management. Despite DHCP’s relative simplicity, things can go wrong. Whether you’re facing IP conflicts or server authorization issues, the following guide aims to address the most common DHCP problems and their solutions.
Issue 1: DHCP Server Not Responding
- Clients unable to obtain IP addresses
- Server status showing as inactive or disabled
- Check the server’s network connectivity.
- Restart the DHCP service:
- Verify firewall rules to ensure DHCP traffic is allowed.
Issue 2: IP Address Conflicts
- Network instability
- Error messages indicating IP address conflict on client machines
- Review DHCP leasing table to identify duplicates.
- Delete conflicting leases from the DHCP server.
- Check for statically assigned IPs that may conflict with the DHCP scope.
Issue 3: Limited IP Addresses Available
- New devices unable to join the network
- DHCP scope exhaustion warnings
- Extend the DHCP scope to include additional IP ranges.
- Decrease lease time to release unused IP addresses faster.
Issue 4: Incorrect DHCP Options
- Incorrect DNS settings
- Wrong gateway configuration
- Verify and modify DHCP options like DNS servers, default gateway, and more.
- Renew leases on client machines to apply the new settings.
Issue 5: Unauthorized DHCP Servers
- Unpredictable network behavior
- Multiple DHCP servers detected on the network
- Identify unauthorized servers using network scanning tools.
- Remove or authorize the rogue DHCP servers.
Issue 6: Lease Time and Renewal Issues
- Frequent disconnections
- Lease not renewing automatically
- Check and adjust the default and maximum lease time settings.
- Restart the DHCP service to apply the changes.
Issue 7: DHCP Server Authorization Issues (Windows only)
- Server failing to issue addresses
- Server status shows as unauthorized
- Open DHCP Management Console.
- Right-click the server and choose “Authorize.”
- Wait for the server to be authorized; this may take a few minutes.
General Tips:
- Always check server logs for more detailed error information.
- Utilize network monitoring tools to watch DHCP traffic and identify irregularities.
By understanding these common DHCP issues and their resolutions, you’ll be better prepared to manage and maintain a reliable network. Troubleshooting is part and parcel of network management, and mastering it can save you both time and resources.
19. Use-Case: DHCP in a Home Network
The setting:.
In a typical home network, the Dynamic Host Configuration Protocol service often resides in the wireless router that provides Internet access. Devices like smartphones, laptops, smart TVs, and IoT gadgets connect to this network.
How It Works:
- Device Connection : When a new device connects to the Wi-Fi, it sends a DHCP Discover message.
- IP Allocation : The router’s DHCP server responds with an Offer message, providing an available IP address.
- Lease Time : Home networks usually have longer lease times (24 hours or more) due to fewer devices and less frequent changes.
- Other Settings : Along with the IP address, the DHCP server often provides additional information like the default gateway (usually the router itself) and DNS servers.
Why It’s Ideal:
- Simplicity : For non-tech-savvy individuals, DHCP automates network configurations, making it user-friendly.
- Resource-Efficient : Home networks rarely exhaust the IP pool, making DHCP a resource-efficient solution.
20. Use-Case: DHCP in Enterprise Networks
Enterprise networks are considerably more complex, consisting of multiple VLANs, subnets, and potentially hundreds or thousands of connected devices. Here, a dedicated DHCP server, or even multiple servers, is common.
- DHCP Scopes : For different subnets and VLANs, administrators define multiple scopes.
- Load Balancing : In larger setups, DHCP services might be distributed across multiple servers for load balancing.
- Lease Time : Generally shorter than in home networks to accommodate the frequent addition and removal of devices.
- Options : DHCP options may include complex settings, such as VoIP configurations, multiple gateway addresses, or even vendor-specific information.
Scaling Techniques:
- DHCP Relay : Allows DHCP servers to provide IP addresses across different subnets or VLANs.
- Failover : Multiple DHCP servers share responsibility, providing high availability.
- Reservation : For critical devices like servers and printers, reserved IP addresses are set.
- Flexibility : DHCP can be fine-tuned to meet the specific requirements of an enterprise network.
- Efficiency : Centralized management makes it easier to apply network policies.
21. Advanced Dynamic Host Configuration Protocol Features
While DHCP is often employed for its basic functionality of assigning IP addresses, it has the capability to do much more. Here are some advanced features that you may encounter or implement in sophisticated network environments.
DHCP Snooping
- What it is : A security feature that filters out unauthorized DHCP messages.
- Why it’s Important : Helps to mitigate rogue DHCP server attacks.
Dynamic DNS Updates
- What it is : Automatic DNS record updating when DHCP assigns a new IP address.
- Why it’s Important : Simplifies DNS management, particularly useful in large networks.
Option 82 – Relay Agent Information
- What it is : A field added by DHCP relay agents, used for policy implementation or logging.
- Why it’s Important : Allows network operators to associate leases with specific client attributes.
Vendor-Specific Information
- What it is : Option 43 allows vendors to pass proprietary parameters to Dynamic Host Configuration Protocol clients.
- Why it’s Important : Enables specialized configurations, such as VoIP phone settings.
- What it is : A feature that prevents unauthorized devices from acting as DHCP servers.
- Why it’s Important : Strengthens network security by blocking rogue DHCP servers.
22. Video Explainer: How Your PC Gets Its IP Address?
A small video explaining the concept of DHCP, an application-layer protocol that your own computer probably uses to get an IP address from your network.
23. Further Reading
To further expand your knowledge and understanding of Dynamic Host Configuration Protocol, the following resources are highly recommended:
- “ DHCP Handbook ” by Ralph Droms and Ted Lemon
- “ TCP/IP Network Administration ” by Craig Hunt
RFCs (Request for Comments)
- RFC 2131 – Dynamic Host Configuration Protocol
- RFC 3046 – DHCP Relay Agent Information Option
Academic Papers
- “ Security Risks in Asynchronous Web Servers : When Performance Optimizations Amplify the Impact of Data-Oriented Attacks”
These materials will provide you with the technical background, implementation guidelines, and a deep understanding of the protocol’s internals, offering both historical context and insights into future developments.


Partner Overview
Join Us for Growth, Innovation and Cybersecurity Excellence.
Become a Channel Partner
Be a Valued Partner and Embark on a Journey of Profitability.
Partner Portal
Unified Security Platform
Latest Content and Resources
Threat Report 2023
NRGi Holding Case Study
What Is Dynamic Host Configuration Protocol (DHCP)?
Last updated on February 20, 2023
DHCP, or Dynamic Host Configuration Protocol, is a network protocol that allows devices on a network to be automatically assigned an IP address. DHCP is used extensively in both home and enterprise networks, as it simplifies the process of configuring IP addresses for new devices.
In this article, we will have a closer look at how DHCP works, what are its main components, its benefits, and we will also analyze some of the security concerns associated with it. Let’s begin!
What Is DHCP?
Dynamic Host Configuration Protocol (DHCP) is a network management protocol that is used to dynamically assign IP addresses and other information to each host on the network in order for them to communicate effectively.
DHCP automates and centrally administers IP address issuance, simplifying network administrators’ work. In addition to the IP address, DHCP assigns the subnet mask, default gateway, domain name server address, and other configurations to the host, making the network administrator’s job much easier.
What Is an IP Address?
An IP address is a unique number assigned to every computer and device on the Internet. IP addresses are used to uniquely identify computers and other networked devices. An IP address can be issued to a computer in two ways: either statically, or dynamically.
Assigning an IP address to a computer or other device manually, as was done in the early days of networking, is called using a static IP . Due to the complexity of this task, especially for large networks, a new way of assigning IP addresses emerged – the DHCP.
Assigning an IP address to a computer/device automatically and temporarily (is then replaced by a new one after its allocated time has passed), with the help of a server that supports the Dynamic Host Configuration Protocol – is called using a dynamic IP.
A DHCP server automatically assigns a computer with:
- An IP address;
- A subnet mask;
- Default gateway;
- And a DNS server.
A Brief History of DHCP
Dynamic Host Configuration Protocol (DHCP) was first defined in RFC 1531 (published in October 1993). The most recent version of the DHCP specification is RFC 2131 (published in March 1997). According to Javatpoint , DHCP is based on the Bootstrap Protocol (BOOTP), which was developed for diskless workstations. If there are any BOOTP clients on a network segment, DHCP servers can handle BOOTP client requests because DHCP is more advanced.
BOOTP introduced the idea of a relay agent that allowed BOOTP packets to be relayed across networks, using one central BOOTP server to serve hosts on numerous IP subnets. BOOTP, however, lacked a mechanism for reclaiming IP addresses no longer in use and required a manual process to add configuration details for each client.
Most home and small office routers support DHCP, and will automatically assign IP addresses to devices connected to the router’s LAN port(s). Many routers also have a “DHCP reservation” feature that allows you to statically assign an IP address to a specific device by its MAC address.
How Does DHCP Work?
DHCP works its ‘magic’ by automating the process of configuring devices on IP networks so that they can access network services including Domain Name System (DNS) , Network Time Protocol (NTP), and any communication protocol based on UDP or TCP .
To facilitate communication between different IP networks, a DHCP server dynamically assigns an IP address and other network setup parameters (subnet mask, default gateway, DNS server) to each device on a network.
DHCP is a service that runs on a server. For instance, this could be a Microsoft or a Linux server, but it could also run on other routers such as a business router or a home router – each of these routers will have a DHCP service built into them.
The DHCP Process
When a computer or device on a network wants to connect to and communicate with others, locally or over the Internet, it operates in a four-step process – also known as DORA process , which stands for:
- Discovery – The first message produced during server and client connection is known as the DHCP discovery request. To find out whether a network has any DHCP servers or servers at all, the client host generates this message. To locate the DHCP server, this message is broadcast to all connected devices in the network.
- Offer – When the server receives the request, it forwards it to its DHCP service. The DHCP service on the server checks the list of available IP addresses that have not already been claimed by other computers and devices. As soon as the DHCP server identifies a free IP address, it sends it to the computer or device that requested it. This step is referred to as a DHCP offer.
- Request – The PC or device receives the dynamically assigned IP address and sends a message back to the DHCP server confirming that it wants to use that IP address. This step is referred to as a DHCP request message because the client requests the offered IP address.
- Acknowledgment – When the DHCP server gets the message request, it sends a final message to the computer or device that started the whole process. This message is known as DHCP acknowledgment, and it has all the other configuration information, such as the gateway address and the addresses of the DNS servers, that is needed to give the computer or device access to the network. This configuration information also provides the time period for which the allocation is valid, known as a lease.
Lastly, the DHCP server or router marks the IP address as being used by the computer or device that requested it. This means that the computer or device can now interact with other devices on the local network and access the Internet.
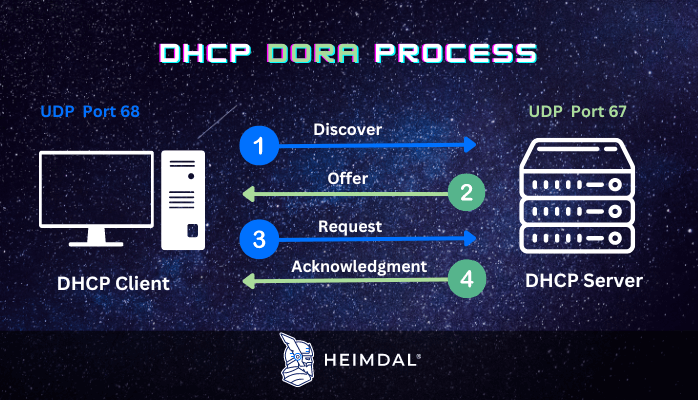
DHCP Uses UPD Port Numbers 67 and 68
DHCP uses the User Datagram Protocol (UDP), a connectionless service model. It works with two UDP port numbers that are the same as the ones for the bootstrap protocol (BOOTP). The server listens on UDP port number 67, and the client listens on port number 68.
DHCP Lease Process
If a client is using dynamic DHCP, the IP address it receives is not its permanent address; rather, it is a temporary lease. A dynamic IP address requires a device to contact a DHCP server whenever it is turned on so that it can obtain a new IP address.
DHCP Components
For a better understanding of Dynamic Host Configuration Protocol (DHCP), let’s also take a closer look at its components:
- DHCP Server. A DHCP server is a networked device that runs the DCHP service and stores IP addresses and related configuration data. Typically, this is a server or a router, but it might be anything that operates as a host, such as an SD-WAN device.
- DHCP Client. The DHCP client is the endpoint that is configured using data sent from a DHCP server. Any network-capable gadget, such as a desktop, notebook, or endpoint for an Internet of Things (IoT) system, would qualify. By default, most gadgets are set up to get their IP address from a DHCP server.
- DHCP Relay. A DHCP relay is a host or router that scans the network for broadcast client messages and forwards them to a specified server. The relay agent subsequently provides responses to the client, who receives them from the server. Instead of having a server on each subnet, DHCP servers can be centrally managed via DHCP relay.
- IP Address Pool. The range of IP addresses that DHCP clients can use is called the IP address pool. IP addresses are normally assigned in descending order from lowest to highest.
- Subnet. The partitioned segments of IP networks are referred to as subnets. Subnets are used to organize networks and make maintenance easier.
- Lease. The lease is the amount of time that a DHCP client keeps the IP address information. When a client’s lease is up, they have to renew it.
DHCP Benefits
DHCP provides numerous benefits that make it an essential component of any successful network. Perhaps most importantly, DHCP can significantly reduce the amount of time and effort required to configure and manage network IP address settings. Other advantages are:
- Centralized IP Address Management: By using DHCP, a network administrator can automatically and centrally manage the IP addresses on their network. With all configuration data stored in a single location, the administrator can manage all IP addresses more efficiently.
- Dynamic host configuration : By automatically assigning IP addresses to devices on a network, DHCP can eliminate the need for manual configuration of these settings – saving valuable time and resources. DHCP also provides a way to automatically assign IP addresses to new devices that are added to a network, making it easier to expand the network without having to manually configure each new device.
- Flexibility : When using DHCP, the administrator has more flexibility because it is simple to switch IP configurations when the infrastructure changes – for example, when a client’s access point changes.
- IP Optimization : Addresses that are no longer in use are free to be reassigned to new network clients.
- Faster Connectivity for Users: One of the benefits of DHCP is that it provides faster connectivity for users. When a user connects to a network, they are assigned an IP address automatically. This eliminates the need for users to manually configure their IP addresses, which can be time-consuming and error-prone.
DHCP Security Concerns
When it comes to networking, DHCP is a core protocol that is responsible for assigning IP addresses to devices. But while DHCP can be incredibly useful, it also poses some security risks that need to be considered.
DoS Attacks
One of the biggest security risks of DHCP is the potential for denial of service (DoS) attacks . An attacker can launch a denial of service attack by sending fake DHCP requests to the server, leasing up all the available IP addresses and leaving no IPs for legitimate clients to use. Alternatively, an attacker could send fake requests and responses to trick clients into connecting to their machine rather than a legitimate DHCP server.
If an attacker is able to send malicious requests to a DHCP server, they can cause it to become overwhelmed and unable to respond to legitimate requests. This can result in network outages and disruptions.
Rogue DHCP Servers
Another risk that needs to be considered is the possibility of rogue DHCP servers. If an attacker is able to set up their own DHCP server on a network, they could assign addresses that conflict with those assigned by the legitimate DHCP server. This could cause problems with connectivity and lead to devices being unable to communicate with each other properly.
How Can Heimdal® Help?
It’s important to be aware of these risks above when using DHCP and take steps to mitigate them. For example, using access control lists (ACLs) on DHCP servers can help prevent unauthorized devices from making requests.
Additionally, monitoring network traffic for suspicious activity can help detect rogue DHCP servers or attempts at DoS attacks. For the latter, we have an excellent product that keeps your endpoints secure by filtering network traffic.
Heimdal Threat Prevention scans your users’ traffic in real-time, blocking infected domains and stopping communication with cybercriminal infrastructures. This gives administrators full confidence and allows users to browse the Internet safely, whether they are on-site or remote, with minimal system footprint.
Threat Prevention can detect malicious processes and URLs, as well as trace the attacker’s origins. Give your staff the right tools, and you’ll have comprehensive visibility and control over your endpoints and network. It works in tandem with any existing antivirus product to block harmful domains as well as communications to and from C2 centers and other malicious servers.
Heimdal® DNS Security Solution
- Machine learning powered scans for all incoming online traffic;
- Stops data breaches before sensitive info can be exposed to the outside;
- Advanced DNS, HTTP and HTTPS filtering for all your endpoints;
- Protection against data leakage, APTs, ransomware and exploits;
Wrapping Up
DHCP is an important protocol for managing networks, but it also carries with it a number of potential security risks. By understanding what DHCP is, how it works, and the possible vulnerabilities associated with its use, users can better protect their systems from unwanted intrusions. With proper configuration and attention to security best practices, DHCP can be used safely and effectively in any network environment.
If you liked this article, follow us on LinkedIn , Twitter , Facebook , Youtube , and Instagram for more cybersecurity news and topics.
Madalina Popovici
Digital PR Specialist
Madalina, a seasoned digital content creator at Heimdal®, blends her passion for cybersecurity with an 8-year background in PR & CSR consultancy. Skilled in making complex cyber topics accessible, she bridges the gap between cyber experts and the wider audience with finesse.
Related Articles
Leave a Reply (Cancel Reply)
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
CHECK OUR SUITE OF 11 CYBERSECURITY SOLUTIONS
- Cyber Resources And Beginners
- Cyber Security Glossary
- The Daily Security Tip
- Cyber Security For Small Business Owners
- Cybersecurity Webinars
- About Heimdal®
- Press Center
- Partner with us
- Affiliate Program
© 2024 Heimdal ®
Vat No. 35802495, Vester Farimagsgade 1, 2 Sal, 1606 København V
Red Hat OpenShift 101 for OpenStack admins: Operators and prerequisites

Red Hat OpenStack Services on OpenShift (RHOSO) service providers can scale faster and maximize their resources. By integrating Kubernetes with OpenStack, organizations see improved resource management and scalability, greater flexibility across the hybrid cloud, simplified development and DevOps practices, and more.
In this article, we’ll cover some of the finer points of OpenShift for OpenStack admins, including the three Red Hat OpenShift Container Platform operators that are prerequisites: cert-manager, MetalLB, and NMstate.
What is an Operator?
An Operator is a method of packaging, deploying, and managing a Kubernetes/OpenShift application. An OpenShift/Kubernetes application is both deployed on OpenShift/Kubernetes and managed using the OpenShift/Kubernetes APIs and oc or kubectl tooling. Operators implement and automate common tasks related to an application's lifecycle, such as deployment, scaling, and backup/restore, by extending Kubernetes's capabilities.
Operators work by watching for resource changes in an OpenShift/Kubernetes cluster and taking specific pre-programmed actions to achieve or maintain a desired state. They leverage Custom Resources (CRs) to introduce new resource types representing a specific application or service configuration. The Operator reacts to changes to these resources, as well as changes to their status, to manage the application.
The concept of an Operator was introduced by CoreOS and is built on three key principles:
- Application-specific knowledge encoded into software : Operators know how to deploy, configure, manage, and troubleshoot the applications they manage. This knowledge, typically acquired by human operators, is codified into the software.
- Declarative application management : Users interact with Operators through Kubernetes APIs and declarative specifications, using tools like kubectl and YAML or JSON manifests to manage applications.
- Level-based, not edge-based logic : Operators take actions to reconcile the current state of the application with the desired state expressed by the user, rather than responding to discrete events. This approach is more resilient and adaptive to changes in the environment.
Operators are particularly useful for stateful applications that require complex setup, scaling, configuration, and maintenance routines. They help to automate the operational complexity that would otherwise require manual intervention, making these tasks more manageable, reliable, and repeatable within the OpenShift/Kubernetes ecosystem.
For more information, see What are Red Hat OpenShift Operators?
OpenShift Container Platform prerequisites
On a base OpenShift Container Platform installation, RHOSO requires 3 operators to be added:
- cert-manager
Cert-manager
With cert-manager, a Kubernetes add-on automates the management and issuance of TLS certificates within Kubernetes clusters. It simplifies the process of obtaining, renewing, and using SSL/TLS certificates from various certificate authorities (CAs), including public ones like Let's Encrypt, as well as private CAs. cert-manager enables users to ensure their applications are securely served over HTTPS without manually managing certificate lifecycles.
Key features of cert-manager include:
- Automated certificate management : Automatically issues and renews certificates based on Kubernetes resources and annotations. It handles the lifecycle of certificates, ensuring they are valid and up-to-date.
- Support for multiple issuers : Works with various CAs, including Let's Encrypt for free, automated certificates, as well as self-signed certificates and private CAs for more controlled environments. It allows for defining different issuers according to specific needs.
- Integration with DNS and HTTP : Automates the ACME (Automated Certificate Management Environment) challenge process required for issuing certificates, supporting both DNS01 and HTTP01 challenge mechanisms.
- Custom Resource Definitions (CRDs) : Extends Kubernetes API with custom resources for managing certificates ( Certificate ), issuers ( Issuer and ClusterIssuer ), and more, allowing for declarative configuration of certificates and their properties.
- Secures Ingress resources : Easily secures Kubernetes Ingress resources by automatically obtaining and renewing certificates and applying them to Ingresses for secure HTTP traffic.
cert-manager is designed to be used in environments where automated certificate provisioning is essential for operational efficiency and security compliance, making it a critical component for securing communication within OpenShift/Kubernetes clusters.
MetalLB is a load balancer implementation for bare metal Kubernetes clusters, providing a network load balancing solution that integrates with standard network equipment. In environments where external load balancers like those provided by cloud providers (AWS ELB, Google Cloud Load Balancer, etc.) are unavailable, MetalLB fills that gap by offering load-balancing services.
Kubernetes does not include a built-in network load balancer for bare metal clusters (non-cloud environments). When you create a Service of type LoadBalancer in a Kubernetes cluster running in a cloud environment, the cloud provider will automatically provision an external load balancer that directs traffic to the Service. However, in a bare metal cluster, without MetalLB, a Service of type LoadBalancer would remain in the "pending" state indefinitely, because there would be no default implementation to handle these types of Services.
MetalLB solves this by providing two major modes of operation:
- Layer 2 Mode : In this mode, MetalLB responds to Address Resolution Protocol (ARP) requests for the IP address of the Service, essentially "claiming" the IP address on the local network. When a client sends traffic to that IP address, MetalLB forwards the traffic to one of the Service's Pods. This mode is simpler but requires all cluster nodes to be on the same L2 network segment.
- BGP (Border Gateway Protocol) Mode : MetalLB can also integrate with BGP-capable routers in your network. In this mode, MetalLB dynamically advertises the Service IP addresses to the routers using BGP, allowing the traffic to be routed to the cluster dynamically. This more complex and powerful mode allows for more scalable and dynamic routing configurations.
With OSO, we use the L2 layer mode.
MetalLB file format
In our OSO DevPreview, our file is minimal to create a single instance of a metallb resource, as a Custom Resource Definition (CRD):
Here's a breakdown of what this MetalLB resource does:
- apiVersion: metallb.io/v1beta1 : This indicates the API version of the MetalLB resource.
- kind: MetalLB : Specifies that the resource is of type MetalLB, indicating that it's a custom resource definition (CRD) provided by MetalLB for configuring the load balancer within the Kubernetes cluster. This is part of MetalLB's move towards custom resources for configuration, allowing for more structured and Kubernetes-native configurations.
- metadata : Contains metadata about the MetalLB resource.
- name: metallb : The name of the MetalLB resource. This name is used to identify the resource within the Kubernetes namespace.
- namespace: metallb-system : Specifies the namespace where MetalLB is deployed. The metallb-system namespace is typically used for MetalLB's components, isolating them from other workloads in the cluster.
This essentially declares an instance of MetalLB to be deployed in the metallb-system namespace. However, without the specification section ( spec: ), it doesn't detail how MetalLB should be configured (e.g., which IP address pools to use, whether to operate in Layer 2 or BGP mode, etc.).
When using MetalLB with the API version ( apiVersion: metallb.io/v1beta1 ) and deploying it through a MetalLB custom resource (CR), you typically need to define IPAddressPool and L2Advertisement resources to configure MetalLB's operation in Layer 2 mode. You would have guessed that we will find these definitions, respectively, in the osp-ng-metal-lb-ip-address-pool and osp-ng-metal-lb-l2-advertisement yaml files.
The NMState Operator in OpenShift is a Kubernetes Operator that provides a declarative way to manage node network configurations across an OpenShift cluster. It utilizes the Node Network Configuration Policy (NNCP) to drive the desired network state across cluster nodes, leveraging the NMState project under the hood.
NMState is an open source project that aims to provide a unified way to perform network configurations using declarative syntax. It allows users to describe network interfaces, IP routing, and other network settings in a declarative manner using YAML or JSON formats. The NMState project simplifies network management tasks, making them more consistent and easier to automate.
Key features of the NMState Operator:
- Declarative network configuration : Enables users to define the desired state of network interfaces, bridges, VLANs, and other network settings in a declarative manner, using YAML. This simplifies the process of configuring, managing, and maintaining network settings across nodes in the cluster.
- Cluster-wide network management : Provides a way to apply network configurations across all nodes in an OpenShift cluster or to a subset of nodes, ensuring consistency in network setups.
- Automated application : Once a Node Network Configuration Policy is defined and applied, the NMState Operator automatically enforces the desired network state on the specified nodes, handling the application and rollback of configurations as needed.
- Status reporting : Reports the current network configuration status and any errors encountered during the application of policies, aiding in troubleshooting and ensuring visibility into network configurations.
- It can be used to ensure consistent network settings across all nodes, and is especially useful in large clusters or when applying standardized configurations. It can also help automate the setup of complex network configurations, such as when bonding interfaces, creating VLANs, or setting up bridges, which might otherwise require manual intervention on each node. Additionally, it can quickly apply changes to network configurations in response to evolving requirements or addressing issues without requiring manual adjustments on individual nodes.
Administrators define a NodeNetworkConfigurationPolicy resource that specifies the desired network state. The NMState Operator watches for these policies and applies the specified network configurations to the nodes, leveraging the Linux NetworkManager and the NMState library. Nodes report back the current state of their network configurations, which can be viewed through the policy status, helping administrators verify the applied configurations.
Now that we have overseen the required operators, their roles, and the format used to create the OpenStack control plane, let’s return to the deployment process. That is the subject of the next article: Red Hat OpenShift 101 for OpenStack admins: Configuration
- Red Hat Enterprise Linux
- Red Hat OpenShift
- Red Hat Ansible Automation Platform
- See all products
- See all technologies
- Developer Sandbox
- Developer Tools
- Interactive Tutorials
- API Catalog
- Operators Marketplace
- Learning Resources
- Cheat Sheets
Communicate
- Contact sales
- Find a partner
Report a website issue
- Site Status Dashboard
- Report a security problem
RED HAT DEVELOPER
Build here. Go anywhere.
We serve the builders. The problem solvers who create careers with code.
Join us if you’re a developer, software engineer, web designer, front-end designer, UX designer, computer scientist, architect, tester, product manager, project manager or team lead.
Red Hat legal and privacy links
- About Red Hat
- Contact Red Hat
- Red Hat Blog
- Diversity, equity, and inclusion
- Cool Stuff Store
- Red Hat Summit
- Privacy statement
- Terms of use
- All policies and guidelines
- Digital accessibility

COMMENTS
Which protocol automates assignment of IP addresses on a network, and which port number does it use? (Choose two.) ... 16. A client device on an Ethernet segment needs an IP address in order to communicate on the network. A DHCP server with IP address 192.168.1.1 has been configured and enabled on the network. How will a client device obtain a ...
What is DHCP. DHCP is a network protocol that is used to automate the process of assigning IP addresses to devices on a network. Prior to the introduction of DHCP, network administrators had to manually configure each device with a unique IP address, which was a time-consuming and error-prone process. DHCP allows devices to automatically obtain ...
Answer : The Dynamic Host Configuration Protocol (DHCP) is used to automatically assign IP addresses to hosts. DHCP is designed to reduce the administrative burden and complexity of manually configuring IP addresses for networked devices. A device connects to the network and broadcasts a DHCP discovery message.
DHCP is a network protocol that automates assigning IP addresses and other essential network configuration parameters, such as DNS settings, ... (Dynamic Host Configuration Protocol), designed for dynamic IP address assignment. It communicates with client devices to provide IP addresses and related information.
DHCP automates the process of assigning IP addresses to devices connecting to a network, making it easier to connect multiple devices. DHCP allows you to control the range of IP addresses available for use, ensuring you can limit the number of devices connected to your network. While DHCP assigns IP addresses temporarily, static IP addresses ...
DHCP is an under-the-covers mechanism that automates the assignment of IP addresses to fixed and mobile hosts that are connected wired or wirelessly. When a device wants access to a network that ...
November 11, 2023. by. Editorial Team. in. Acronyms, Letter D, Network Protocols. Dynamic Host Configuration Protocol (DHCP) is a network protocol used to dynamically assign IP addresses and other network settings to devices on a local network. This comprehensive article aims to demystify DHCP, delving into its core components, mechanisms, and ...
Dynamic Host Configuration Protocol (DHCP) is a network management protocol that automates the assignment of IP addresses. DHCP assigns networking parameters such as subnet mask, default gateway address, and DNS. When using DHCP, a device goes through the following steps: Droplets created from custom images use DHCP to obtain an IP address from ...
To configure the server, first, choose the IP address of the network you're going to use. In our case, we're going to take the network 1.0.0.0/8. Then, follow the different configuration steps: Configure an IP address on the server. We can use 1.0.0.1, for example. Activate the DHCP service. Configure the IP address range to assign to the ...
Dynamic Host Configuration Protocol (DHCP) is a network management protocol that is used to dynamically assign IP addresses and other information to each host on the network in order for them to communicate effectively. DHCP automates and centrally administers IP address issuance, simplifying network administrators' work.
Study with Quizlet and memorize flashcards containing terms like Which protocol automates assignment of IP addresses on a network, and which port number does it use? (Choose two.) DHCP DNS SMB 53 67 80, Refer to the exhibit. PC1 is configured to obtain a dynamic IP address from the DHCP server.
In our network devices, IP addresses can be assigned in 2 ways, statically or via DHCP. Static IP address assignment is added by an operator via CLI, or a script pushing automating configurations. Dynamic Host Configuration protocol or DHCP, allows a host or interface to request am IP address from a pool. In this demo, we will see both options ...
Which protocol automates assignment of IP addresses on a network, and which port number does it use? (Choose two.) DHCP DNS SMB 53 67 80. Click the card to flip 👆 ... Which command will allow a network administrator to check the IP address that is assigned to a particular MAC address?
Study with Quizlet and memorize flashcards containing terms like Which protocol automates assignment of IP addresses on a network, and which port number does it use? (Choose two.), Which FHRP implementation is a nonproprietary IPv4-only election protocol which has one master router per group?, Match each DHCP message type with its description. (Not all options are used.) and more.
-A DNS server., Which protocol automates assignment of IP addresses on a network, and which port number does it use? (Choose two.) -DNS -DHCP -53 -67 -80 -SMB and more. Study with Quizlet and memorize flashcards containing terms like Which message does an IPv4 host use to reply when it receives a DHCPOFFER message from a DHCP server?
Engineering. Computer Science. Computer Science questions and answers. Which protocol automates assignment of IP addresses on a network, and which port number does it use? (Choose two.) Group of answer choices A) 68 b) 66 c) DHCP D) DNS E) 53. Question: Which protocol automates assignment of IP addresses on a network, and which port number does ...
Study with Quizlet and memorize flashcards containing terms like Which protocol automates assignment of IP addresses on a network, and which port number does it use?, Know the order (DORA), A company uses DHCP servers to dynamically assign IPv4 addresses to employee workstations. The address lease duration is set as 5 days. An employee returns to the office after an absence of one week. When ...
567 likes, 14 comments - htrooot on May 8, 2024: "Diving into DHCP: Simplifying Network Configuration! Explore How Dynamic Host Configuration Protocol Automates IP Address Assign...". Hack To Root | Diving into DHCP: Simplifying Network Configuration! 🌐💻 Explore How Dynamic Host Configuration Protocol Automates IP Address Assign ...
Integration with DNS and HTTP: Automates the ACME ... Layer 2 Mode: In this mode, MetalLB responds to Address Resolution Protocol (ARP) requests for the IP address of the Service, essentially "claiming" the IP address on the local network. When a client sends traffic to that IP address, MetalLB forwards the traffic to one of the Service's Pods.
Which protocol automates assignment of IP addresses on a network, and which port number does it use? (Choose two.) - DHCP - DNS - SMB - 53 - 67 - 80 ... Any other device on the same network that receives an address in the same range is reachable. ...
Terms in this set (14) Study with Quizlet and memorize flashcards containing terms like Provides connections to computers over a TCP/IP network, Sends email over a TCP/IP network, Translates URLs to IP address and more.