Red Green Repeat Adventures of a Spec Driven Junkie
Understanding assignment branch condition.
Recently, I integrated Rubocop into my work flow and it’s been very humbling. I feel I’m a great coder with all the specs passing and doing a good job of refactoring, Rubocop always finds something wrong with my code.
I usually go back and make fixes based on Rubocop’s suggestions, but I keep running into the same few issues and solving them isn’t as easy as using: rubocop -a (which auto-corrects all the easy ones!)
The toughest offense for me so far: Assignment Branch Condition
This offense is harder to fix really make me think about my coding style in general. I want to learn more about this offense to help me understand. By understanding, my goals is to not make this offense so often and/or make it easier for me to fix in the future.

What is: ABC?
Rubocop message:
The default is 15 and the first pass of my code is always way past this, probably on average twice this value. So cleaning up my code to meet the default value really takes a lot of work.
From the documentation :
Really Understanding: ABC
Let’s understand what ABC is by checking out the definition of ABC :
Broken down:
- assignments (anything with = )
- branches (anything that jumps out of the current method)
- conditionals (anything that tests logic if , case , unary ? )
SO, to reduce the ABC value, reduce assignments (use less intermediate variables), fewer branches (calling other methods), and conditionals (if/else statements).
Computing ABC
The ABC value is not just a counting of them, but a square root of the sum of their squares. If any one of them getting too high will spike the ABC count.
The Rubocop default for ABC metric is 15. What does 15 really mean?
Well, doing the math, to get an ABC score of 15, a method would have:
- 8 assignments
- 8 conditionals
(Just working backwards from 15*15 => 225; 225/3 => 75; Math.sqrt(75) ~=> 8.66)
Now that I lay it out that way, an ABC value of 15 is very reasonable. Having eight of each for a method is just enough to do a lot of work in a method, but a value of 15 keeps the method from spiraling out of control in assignments, branches, or conditionals.
Whenever I encountered Rubocop’s ‘ABC is too high’ message, I was annoyed with ABC metric because I didn’t understand how it was computed and I couldn’t refactor efficiently to lower the ABC value quickly.
Now that I spent some effort into researching what Assignment Branch Condition really means, I feel better about creating or refactoring code that has a better ABC score.

DEV Community
Posted on Jun 26, 2020 • Updated on Aug 3, 2020 • Originally published at thedevpost.com
11 Most Asked Questions About RuboCop
RuboCop is a Ruby static code analyzer and code formatter which helps to track errors easily and fix minor code issues during the development process saving your time. It has many advantages and you can learn more about RuboCop on https://docs.rubocop.org/en/stable/ .
Today, we will be talking about the most asked questions about RuboCop.
1. How to check if record exists from controller in Rails
How to test if at least one record exists?
Option 1: Using .exists?
Option 2: Using .present? (or .blank? , the opposite of .present? )
Option 3: Variable assignment in the if statement
This option can be considered a code smell by some linters (RuboCop for example).
Option 3b: Variable assignment
You can also use .find_by_user_id(current_user.id) instead of .where(...).first
Best option:
- If you don’t use the Business object(s): Option 1
- If you need to use the Business object(s): Option 3
Alternative Answer:
In this case, you can use the exists? method provided by ActiveRecord:
2. How to ignore lines with comments?
There is a way to ignore cops on a per-line basis.
There is also a way to do it via the configuration file.
Run rubocop --auto-gen-config and it will generate a file that you can use to disable the offenses.
The command also gives a hint on what to do to load those options.
On a line per line basis, you can enable and disable the cops as well.
You can also do more than one rule at a time in your code.
By using an inline directive, the directive becomes valid only for that line, and it would look like this:
It’s possible to define regex patterns to automatically ignore certain lines in rubocop.yml , so you could choose to ignore all lines starting with a # character:
This could be improved so that “indented” comment lines (i.e. whitespace followed by a # character) is also ignored if that’s what you want.
Note that this doesn’t account for lines of code that end with a comment, though:
3. How to split Ruby regex over multiple lines?
You need to use the /x modifier, which enables free-spacing mode.
Like in this case:
Using %r with the x option is the preferred way to do this.
See this example from the GitHub ruby style guide
4. RuboCop: Line is too long ← How to Ignore?
You can disable a bunch of lines like this:
Or add this to your .rubocop.yml file to increase the max length:
Creating a .rubocop.yml file (keep an eye on the initial . in the filename) in the root of your project, you’ll have a bunch of options:
5. What is meant by ‘Assignment Branch Condition Size too high’ and how to fix it?
Assignment Branch Condition (ABC) size is a measurement of the size of a method. It is essentially determined by counting the number of A ssignments, B ranches, and C onditional statements.
To reduce the ABC score, you could move some of those assignments into before_action calls:
6. How to tell RuboCop to ignore a specific directory or file?
You can add the following to .rubocop.yml:
where the path is relative to .rubocop.yml
From rubocop/default.yml :
7. How to integrate RuboCop with Rake?
The simple answer is just adding this to your Rakefile:
As of version 0.10.0 RuboCop contains a custom rake task that you can use. Just put the following in your Rakefile
Make sure to use upper-case ‘R’ and ‘C’ or you will get a NameError.
8. How to silence RuboCop warning on Assignment Branch Condition?
This is the message for the Metrics/AbcSize cop.
# rubocop:disable Metrics/AbcSize
On your RuboCop config
9. How to disable frozen string literal comment checking?
Add the following to your .rubocop.yml :
10. How to pass &:key as an argument to map instead of a block with Ruby?
Pass &:key as an argument to map instead of a block.
11. How to fix "SublimeLinter-RuboCop not running even when enabled and RuboCop in the path"?
First, specify the right path for you ruby env in Packages/User/SublimeLinter.sublime-settings as this:
After that close sublime completely and reopen it.
In Conclusion
These are the most asked questions about the RuboCop. If you have any suggestions or any confusion, please comment below. If you need any help, we will be glad to help you.
We, at Truemark , provide services like web and mobile app development, digital marketing, and website development. So, if you need any help and want to work with us, please feel free to contact us.
Hope this article helped you.
Original Source: DevPostbyTruemark
Top comments (0)
Templates let you quickly answer FAQs or store snippets for re-use.
Are you sure you want to hide this comment? It will become hidden in your post, but will still be visible via the comment's permalink .
Hide child comments as well
For further actions, you may consider blocking this person and/or reporting abuse

How to use enum attributes in Ruby on Rails
Honeybadger Staff - Mar 4

clsx for Rails views
Leonid Svyatov - Mar 3

Scope vs Class Methods
Trupti - Feb 10

Stimulus é um tesão (ou Como fazer uma navbar responsiva em Rails 7 e Bulma CSS)
Gabriel Gomes de Oliveira - Mar 1

We're a place where coders share, stay up-to-date and grow their careers.
Ruby – How does “Assignment Branch Condition size for index is too high” work
code metrics rubocop ruby
Rubocop is always report the error:
app/controllers/account_controller.rb:5:3: C: Assignment Branch Condition size for index is too high. [30.95/24]
How to fix it? Anyone has good idea?
Best Answer
The ABC size [1] [2] is
computed by counting the number of assignments, branches and conditions for a section of code. The counting rules in the original C++ Report article were specifically for the C, C++ and Java languages.
The previous links details what counts for A, B, and C. ABC size is a scalar magnitude, reminiscent of a triangulated relationship:
Actually, a quick google on the error shows that the first indexed page is the Rubocop docs for the method that renders that message .
Your repo or analysis tool will define a threshold amount when the warning is triggered.
Calculating, if you like self-inflicting....
Your code calcs as
That's a 'blind' calculation with values I've made up ( 1 s). However, you can see that the error states numbers that probably now make sense as your ABC and the threshold:
So cop threshold is 24 and your ABC size is 30.95 . This tells us that the rubocop engine assign different numbers for A, B, and C. As well, different kinds or Assignments (or B or C) could have different values, too. E.G. a 'normal' assignment x = y is perhaps scored lower than a chained assignment x = y = z = r .

tl;dr answer
At this point, you probably have a fairly clear idea of how to reduce your ABC size. If not:
- a simple way it to take the conditional used for your elsif and place it in a helper method.
- since you are assigning an @ variable, and largely calling from one as well, your code uses no encapsulation of memory. Thus, you can move both if and elsif block actions into each their own load_search_users_by_role and load_search_users_by_order methods.
Related Solutions
How to convert to google encoded polyline algorithm format.
The definitive reference to encoding and decoding polylines is by Professor Mark McClure, at http://facstaff.unca.edu/mcmcclur/GoogleMaps/EncodePolyline/
It contains utilities, a discussion of the algorithm and ports of the Javascript code into Perl, Ruby, PHP, Java and Mathematica.
Note: for Version 3, you don't need the levels string which is needed for Version 2. Version 3 works out the levels for itself.
Related Topic
Advancing your Security with IAM Permission Boundaries
Get in touch with advanced iam constructs offered by aws.

Table of contents
Identity & resource-based policies, restricting effective permissions via boundaries, use-case examples, key takeaways.
AWS Identity and Access Management (IAM) enables you to manage access to all identities & resources in a fine-grained and simple way. Besides, the well-known identity and resource-based policies, AWS offers you the advanced feature of Permission Boundaries for restricting the maximum permissions of identities.
Overview of what we’ll talk about:
Quick introduction: identity & resources-based policies
AWS distinguishes between different types of policies. Let’s dive into the most common ones real quick.
On the one hand, there are identity-based policies that are attached to a user, group, or role. The policy documents control which actions can be taken by the identity of which resources. Those can be separated into managed policies — standalone policies, attachable to multiple users, groups or roles — and inline policies — policies with a strict attachment to a single user, group, or role. In our example, we’re adding S3 permissions for a Lambda execution role.
On the other hand, there are resource-based policies that define how a certain principal (e.g. an AWS service) is allowed to access a resource. As the name expects, those policies can be attached to resources, e.g. an S3 bucket. In the following example, we’re granting the role backup of account 1234567890 access to our bucket-keeping backups.
As we’ve covered the basics, let’s get to the interesting part.
As mentioned in the beginning, boundaries are limiting the maximum permissions. They are not providing permissions on their own, but only restricting already granted permissions. So if we need access to S3, we need to explicitly give this permission in our identity or resource-based permission, even if our permission boundary allows this action.
💡 Permission boundaries are not limiting resource-based polices : created boundaries are only able to restrict permissions that are granted to a user by its identity-based policy. Resource-based policies are always granting additional permissions, regardless of what’s inside the permission boundary. Even if it’s an explicit deny .
We can summarize the whole concept in a single diagram:
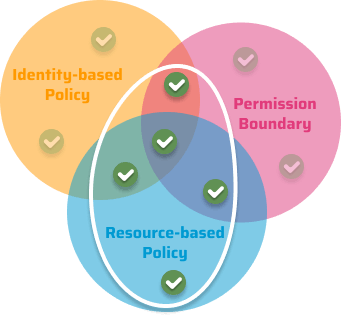
Effective permissions based on identity-based, resource-based & boundary policies
To attach a boundary to a specific role in Terraform, you need to provide it via permissions_boundary . Let’s extend our Lambda execution role from our introduction:
We’re now making sure that only S3 buckets with our expected prefix first- can be accessed. And that’s basically it! You can now create your boundaries based on different conditions and apply those to all users, groups, and roles in your account.
💡 Additional note : if you really want to put effort into your boundary permissions, you can easily exceed the maximum policy size at AWS! So don’t be too specific if you’re making use of a lot of different services. Also, it’s not possible to attach multiple boundary policies to a single role!
There are a lot of really good use cases for permission boundaries. For example, if we’re having multiple, completely independent applications within our AWS account and we want to separate them securely in a programmatic way.
We define that all resources related to our applications will be prefixed with their application name, e.g. application first will have resource names starting with first- , application second will have names starting with second- , and so on.
We’ll also tag accordingly, because for some resources we can’t attach specific names and therefore can only control access based on attached tags, e.g. CloudFront distributions or certificates in ACM.
Now we can create our permissions boundary policy based on our known prefix and/or expected tag and attach this policy as permissions_boundary to all of our roles. Ascertain actions require unrestricted resource access via * , e.g. dynamodb:ListTables , make sure to have this covered in your boundaries.
If we want to use CodeBuild/CodePipeline as our Contentious Integration & Delivery solution, we can also attach our boundary policy to the executive roles of both services as a “normal” policy. With this, we’re granting all of our permissions directly, and also be sure we’re not breaching any boundaries.
Permission boundaries are an awesome way to enhance your account security by settings the maximum viable range of actions. With them, it’s much less likely that you’re granting unnecessary rights, as your having centrally managed boundaries that you can apply to all your users, roles, and groups.
Even if not all of your team is putting great effort into respecting the least privilege, you're still having certain limits covered easily.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Assign Azure roles using the Azure portal
- 4 contributors
Azure role-based access control (Azure RBAC) is the authorization system you use to manage access to Azure resources. To grant access, you assign roles to users, groups, service principals, or managed identities at a particular scope. This article describes how to assign roles using the Azure portal.
If you need to assign administrator roles in Microsoft Entra ID, see Assign Microsoft Entra roles to users .
Prerequisites
To assign Azure roles, you must have:
- Microsoft.Authorization/roleAssignments/write permissions, such as Role Based Access Control Administrator or User Access Administrator
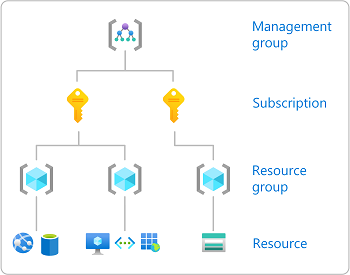
Step 1: Identify the needed scope
When you assign roles, you must specify a scope. Scope is the set of resources the access applies to. In Azure, you can specify a scope at four levels from broad to narrow: management group , subscription, resource group , and resource. For more information, see Understand scope .
Sign in to the Azure portal .
In the Search box at the top, search for the scope you want to grant access to. For example, search for Management groups , Subscriptions , Resource groups , or a specific resource.
Click the specific resource for that scope.
The following shows an example resource group.

Step 2: Open the Add role assignment page
Access control (IAM) is the page that you typically use to assign roles to grant access to Azure resources. It's also known as identity and access management (IAM) and appears in several locations in the Azure portal.
Click Access control (IAM) .
The following shows an example of the Access control (IAM) page for a resource group.

Click the Role assignments tab to view the role assignments at this scope.
Click Add > Add role assignment .
If you don't have permissions to assign roles, the Add role assignment option will be disabled.

The Add role assignment page opens.
Step 3: Select the appropriate role
On the Role tab, select a role that you want to use.
You can search for a role by name or by description. You can also filter roles by type and category.

If you want to assign a privileged administrator role, select the Privileged administrator roles tab to select the role.
For best practices when using privileged administrator role assignments, see Best practices for Azure RBAC .

In the Details column, click View to get more details about a role.

Click Next .
Step 4: Select who needs access
On the Members tab, select User, group, or service principal to assign the selected role to one or more Microsoft Entra users, groups, or service principals (applications).

Click Select members .
Find and select the users, groups, or service principals.
You can type in the Select box to search the directory for display name or email address.

Click Select to add the users, groups, or service principals to the Members list.
To assign the selected role to one or more managed identities, select Managed identity .
In the Select managed identities pane, select whether the type is user-assigned managed identity or system-assigned managed identity .
Find and select the managed identities.
For system-assigned managed identities, you can select managed identities by Azure service instance.

Click Select to add the managed identities to the Members list.
In the Description box enter an optional description for this role assignment.
Later you can show this description in the role assignments list.
Step 5: (Optional) Add condition
If you selected a role that supports conditions, a Conditions tab will appear and you have the option to add a condition to your role assignment. A condition is an additional check that you can optionally add to your role assignment to provide more fine-grained access control.
The Conditions tab will look different depending on the role you selected.
- Delegate condition
- Storage condition
Delegating Azure role assignment management with conditions is currently in PREVIEW. See the Supplemental Terms of Use for Microsoft Azure Previews for legal terms that apply to Azure features that are in beta, preview, or otherwise not yet released into general availability.
If you selected one of the following privileged roles, follow the steps in this section.
- Role Based Access Control Administrator
- User Access Administrator
On the Conditions tab under What user can do , select the Allow user to only assign selected roles to selected principals (fewer privileges) option.

Click Select roles and principals to add a condition that constrains the roles and principals this user can assign roles to.
Follow the steps in Delegate Azure role assignment management to others with conditions .
If you selected one of the following storage roles, follow the steps in this section.
- Storage Blob Data Contributor
- Storage Blob Data Owner
- Storage Blob Data Reader
- Storage Queue Data Contributor
- Storage Queue Data Message Processor
- Storage Queue Data Message Sender
- Storage Queue Data Reader
Click Add condition if you want to further refine the role assignments based on storage attributes.

Follow the steps in Add or edit Azure role assignment conditions .
Step 6: Assign role
On the Review + assign tab, review the role assignment settings.

Click Review + assign to assign the role.
After a few moments, the security principal is assigned the role at the selected scope.

If you don't see the description for the role assignment, click Edit columns to add the Description column.
- Assign a user as an administrator of an Azure subscription
- Remove Azure role assignments
- Troubleshoot Azure RBAC
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources
Search code, repositories, users, issues, pull requests...
Provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement . We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Fix "Rubocop/Metrics/AbcSize" issue in app/models/conversation.rb #62
pranavrajs commented Oct 2, 2019
github-actions bot commented Aug 10, 2022
Sorry, something went wrong.
Successfully merging a pull request may close this issue.
More than 3 years have passed since last update.
RuboCopでこんなエラーが出た。Assignment Branch Condition size for search is too high.
コミットをする前にこんなエラーが出た。 調べてみると、なげーよ、幅取りすぎだろみたいなエラーらしい。
RuboCopとは。簡単に
RuboCopのGithub https://github.com/rubocop-hq/rubocop/tree/v0.28.0
このRubCopはコードを検査してくれるものらしくて、コードが長いとか、インデントが変だとかいろんなことを教えてくれる。勝手に直してくれる(不自然なインデントを修正)ときもあれば、警告文だけだして、自分でどうにかしてくれみたいな時もある。ただ、このRuboCopからの指摘も全てが正しい訳ではないっぽい。
今回のエラーに関して
最初に述べたように、なげーよ的な意味らしい。
実際に指摘を受けたコード
自分でも書いていて、長いなと思った。縦に長い。ただ、今の知識ではどうやってコードをより簡潔なものにすればいいか思いつかなかった。だれか教えてください。
それで結局どうしたか・・・
.rubocop.yml RuboCopの設定を変更した。 エラー文を見てみると、、、、
[<10, 21, 5> 23.79/20] この部分が、点数を表しているっぽい。これでみると、これだと『MAXスコアが20なのにお前のは23.79だよ』ってことらしく、これをどうにかするしかないと思った。
それで、.rubocop.yml内にある設定を変更した。
どう変更したかというと、、、
このMaxの部分を 25に設定を変更した。そしてコミットすると、RubCopからの指摘を受けずにすんだ。
設定変えられるのかー程度に、この記事では感じていただければ、幸いです。
Register as a new user and use Qiita more conveniently
- You get articles that match your needs
- You can efficiently read back useful information
- You can use dark theme

IMAGES
VIDEO
COMMENTS
Assignment Branch Condition (ABC) size is a measurement of the size of a method. It is essentially determined by counting the number of Assignments, Branches, and Conditional statements. (more detail..) To reduce ABC score, you could move some of those assignments into before_action calls:
'Assignment Branch Condition Size too high' is a linting error, produced by a tool performing static code analysis. It indicates that there are too many assignments, branches and conditionals in one method or function.
The toughest offense for me so far: Assignment Branch Condition. This offense is harder to fix really make me think about my coding style in general. I want to learn more about this offense to help me understand. By understanding, my goals is to not make this offense so often and/or make it easier for me to fix in the future.
2. From your example it is clear you don't need many of the intermediary variables and therefore assignments. All the parameters building code that is actually necessary should be moved to a separate method: def send_deliverer_push_notification (order_fulfillment, parse_events) order = Order.find_by (id: order_fulfillment_id) message = "Order ...
In the Azure portal, open Access control (IAM) for the role assignment that has a condition that you want to view, edit, or delete. Click the Role assignments tab and find the role assignment. In the Condition column, click View/Edit. If you don't see the View/Edit link, be sure you're looking at the same scope as the role assignment.
5. What is meant by 'Assignment Branch Condition Size too high' and how to fix it? Answer: Assignment Branch Condition (ABC) size is a measurement of the size of a method. It is essentially determined by counting the number of Assignments, Branches, and Conditional statements.
Assignment Branch Condition (ABC) size is a measurement of the size of a method. It is essentially determined by counting the number of Assignments, Branches, and Conditional statements. (more detail..) To reduce ABC score, you could move some of those assignments into before_action calls:
I have this method which returns the number, but Rubocop said: Assignment Branch Condition size for rating is too high. [15.84/15] def rating response = response_quality if response...
Restricting effective permissions via boundaries. As mentioned in the beginning, boundaries are limiting the maximum permissions. They are not providing permissions on their own, but only restricting already granted permissions. So if we need access to S3, we need to explicitly give this permission in our identity or resource-based permission, even if our permission boundary allows this action.
1 - move the require statements to the top of your file. It's clearer when they're there. Rubocop may be counting them as function calls as well. 2 - split out ARGV in a main method and pass in only the arguments you need. You should have a dedicated function parsing ARGV. It shouldn't be in the middle of a function like this.
Assignment Branch Condition size for hashes #1974. Closed firedev opened this issue Jun 17, 2015 · 7 comments Closed ... Rubocop complaints that assignment branch condition is too high, but there is no actual assignment (apart from hash keys) and certainly no branches or conditions.
Step 1: Identify the needed scope. Step 2: Open the Add role assignment page. Step 3: Select the appropriate role. Show 4 more. Azure role-based access control (Azure RBAC) is the authorization system you use to manage access to Azure resources. To grant access, you assign roles to users, groups, service principals, or managed identities at a ...
Assignment Branch Condition size for push_event_data is too high. [25.51/15] https://codeclimate.com/github/chatwoot/chatwoot/app/models/attachment.rb#issue ...
Assignment Branch Condition size for notify_status_change is too high. [19.92/15] https://codeclimate.com/github/chatwoot/chatwoot/app/models/conversation.rb#issue ...
なにこのエラーAssignment Branch Condition size for search is too high. [<10, 21, 5> 23.79/20] コミットをする前にこん…
My code is working correctly, but is resulting in a "Assignment branch condition too high" warning with a score of 12.08 on CodeBeat. Codebeat is an automated code review utility that helps developers write clean code. I have been using it lately in order to monitor the quality of my code since clean code is being a necessity in today's word.
I am confused here about what RuboCop is complaining about. "Assignment Branch Condition size for draw is too high. [29/15]" for the method below: class Ball attr_reader :color attr_reader :
This cop checks that the ABC size of methods is not higher than the configured maximum. The ABC size is based on assignments, branches (method calls), and conditions.