Networking | Cloud | DevOps | IaC

IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server is an important element to networking in the real world. User location cannot be predicted as they may be at and out of a desk and up and about should they need to do so. Tying them to a local VLAN may only be helpful if they are bound to desks in those locations, although the most ideal outcome, it is not the most practical.
It is only wise to incorporate IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server in areas where you expect different teams to come to. Meeting rooms could for a moment have the accounting group or the development group meeting there and based on the intelligent and dynamic vlan assignmnet with 802.1x authentication, users port-access are defined their appropriate vlans for their respective access to resources on the network.
How to Provision 802.1 X Authentication Step By Step With Dynamic VLAN Assignment With Windows Radius Server For 802.1x Clients.
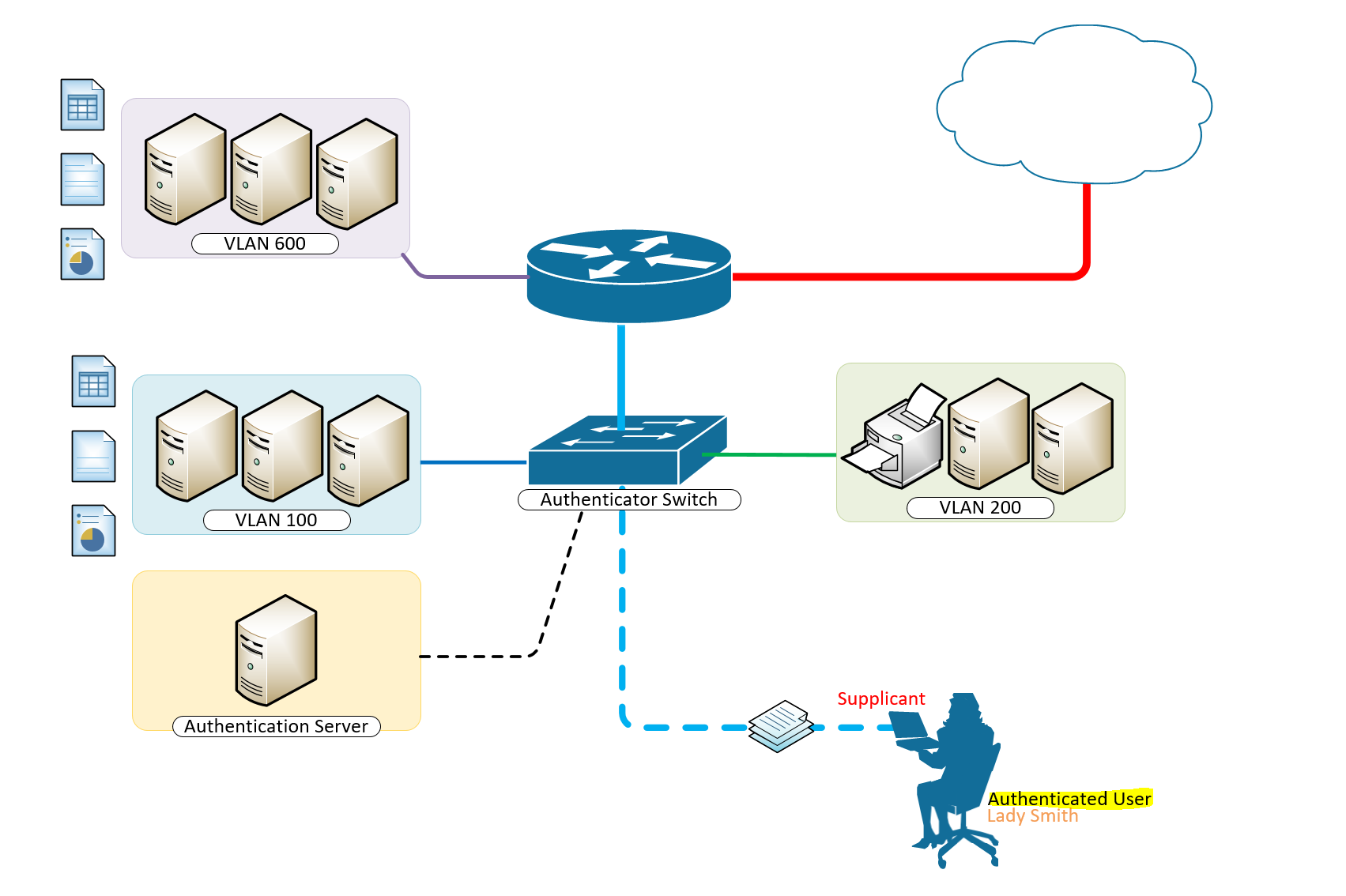
A typical configuration for a system under IEEE 802.1x Authentication control is shown in the following figure.
In this scenario, “Lady Smith” wishes to use services offered by servers on the LAN behind the switch. There are multiple VLANs with resources available based on user vlan membership. Her laptop computer is connected to a port on the Aruba 2920 Edge Switch that has 802.1x port authentication control enabled.
The laptop computer must therefore act in a supplicant role. Message exchanges take place between the supplicant and the authenticator which is the Aruba 2920 Switch, and the authenticator passes the supplicant’s credentials which is her (Windows Active Directory User Account Credentials) to the authentication server for verification. The NPS Server which is the authentication server then informs the authenticator whether or not the authentication attempt succeeded, at which point “Lady Smith” is either granted or denied access to the LAN behind the switch.
Setup Structure for IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
- Supplicant: Laptop running Microsoft Windows 10 or Windows 7
- Authenticator: HP Aruba 2920 Edge Switch
- Authentication Server: Microsoft NPS (Network Policy Server) running on Windows Server 2012 R2.
- User Database : Active Directory
For Windows Infrastructure
Create NPS Server – Add Role on Windows Server 2012 R2
- Create DHCP Scopes for VLANS
Create RADIUS Client on NAC using Network Policy Server
- Create Network Policies
- Configure a Network Policy for VLANs
- Start Wired Auto-Config Service
- Enable Network Authentication
Create the DHCP Scopes for VLAN100 and VLAN200 Groups
- Development Group Scope – VLAN 100
SVI: ip address 172.16.80.254 255.255.255.0 Scope Subnet: 172.16.80.1/24
- Accounting Group Scope – VLAN 200
SVI:ip address 172.16.70.254 255.255.255.0 Scope Subnet: 172.16.70.0/24
Secret Key: secret12
Add Edge Switch Management IP as the RADIUS Client
The Shared Secret Key: secret12 will be used in the Switch Configuration.
Create Network Policy Settings for Accounting Group for VLAN 200
Configuration Example
Here’s an example of how you might consider when configuring Microsoft NPS Server to assign users to a VLAN based on their user group, using NPS for the authentication and authorization of users. This configuration has worked flawlessly on the HP Aruba 2920 Switch. The key to getting this to work is the use of a RADIUS element called: ‘Tunnel-PVT-Group-ID’. This is a RADIUS attribute that may be passed back to the authenticator (i.e. the Aruba 2920 Switch) by the authentication server (i.e. Microsoft NPS Server) when a successful authentication has been achieved. There are a few other elements which need to accompany it, but this is the key element, as it specifies the VLAN number that the user should be assigned to.
The other elements that need to be returned by the NPS Server are as follows:
- Tunnel-PVT-Group-ID: 200
- Service-Type: Framed
- Tunnel-Type: VLAN
- Tunnel-Medium-Type: 802
For Client Infrastructure
On the Supplicant, Windows 7 or 10 configure the following steps on the Ethernet Adapter to enable IEEE 802.1X Authentication
For Network Infrastructure
Connect Server Infrastructure to VLAN 400
Create VLAN for Accounting Group
Create VLAN for Development Group
Create AAA Configuration on Switch for Radius Authentication
Download the Switch Configuration:
Test the IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
Verify Port-Access with the following user groups – VLAN 100 and VLAN 200
Think of what other clever things you can do from the information below;
Breakdown of Commands for RADIUS Authentication
Verification Commands
Thanks for reading. Please share your thoughts in the comment box below;
Published in Configuring , Design , Installing and Configuring , Networking , Security and Switching
- 802.1 x authentication step by step aruba
- 802.1 x authentication step by step cisco
- 802.1 x wireless authentication step by step
- 802.1x authentication process
- 802.1x authentication windows 10
- 802.1x authentication windows server 2012
- 802.1x certificate authentication
- assignment wlc
- cisco dot1x
- cisco ise dynamic vlan
- cisco ise dynamic vlan assignment wlc
- cisco wireless radius attributes
- configuration example
- dynamic vlan assignment cisco 2960 dynamic vlan configuration in packet tracer
- dynamic vlan assignment with windows radius server
- dynamic vlan cisco
- dynamic vlan ruckus
- meraki dynamic vlan assignment
- nps mac authentication wired
- nps policy for mac-based authentication
- radius multiple vlans
- vlan radius server
- vlan steering
- vmps server
Network Guys
Share your knowledge!
How to use 802.1x/mac-auth and dynamic VLAN assignment
Hello guys! Today I want to show you how to secure your edge-switches with 802.1x and mac-authentication fallback in combination with HPE comware-based switches. The 802.1x protocol is used for network access control. For devices like printers, cameras, etc. we will use mac-authentication as a fallback. We will also use dynamic VLAN assignment for the connected ports.
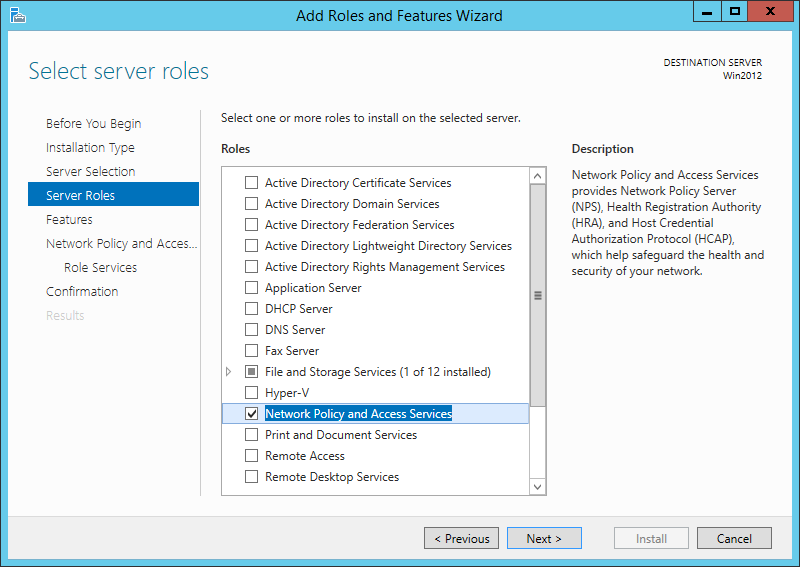
Our radius server will be Microsoft NPS. You can activate this role on the Windows server:
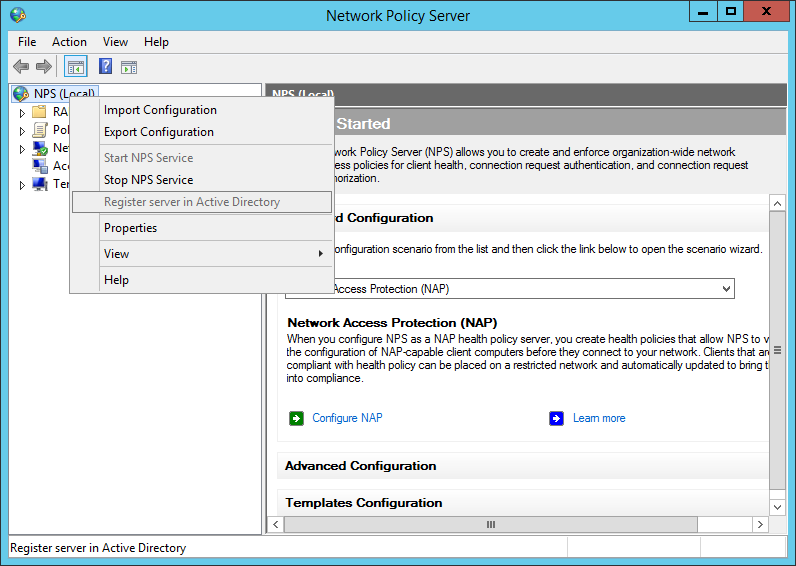
After the installation, open the NPS console and register the radius server in your Active Directory:
add your switches or your management network as a radius-client:
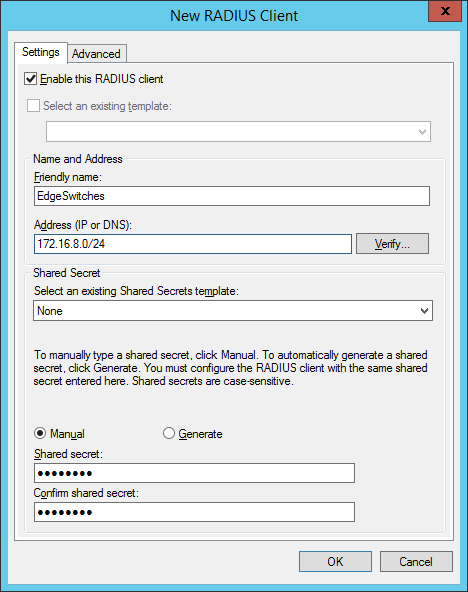
the shared secret will be used in the switch configuration. In created two groups within my test environment:
- “ VLAN2-802.1x ” containing computer accounts
- “ VLAN3-MAC-Auth ” containing user accounts (username+password = mac-address of the device)
So we will now configure two network policies for our network access control:
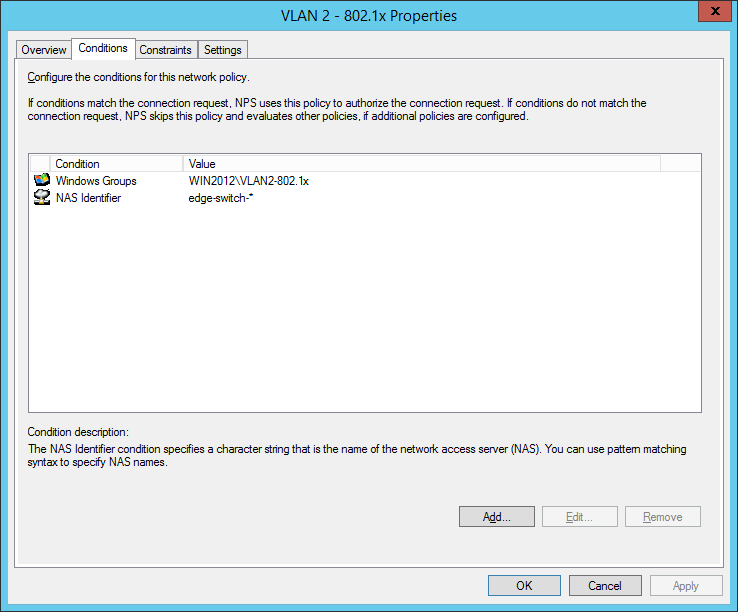
I also configured a NAS Identifier so no other device can use the radius server. The clients will use their computer certificate so you will need a running internal certification authority. Choose PEAP only as the authentication method:
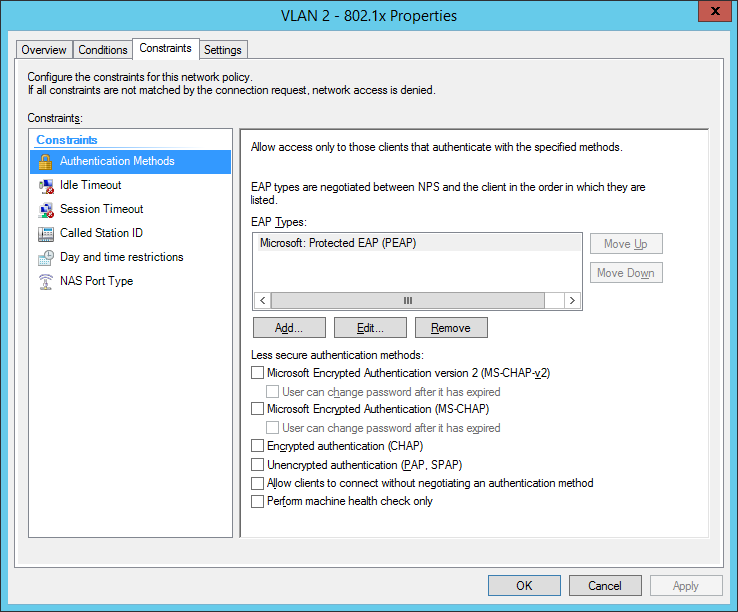
the next step is for our dynamic VLAN assignment. Dot1x devices are bound to VLAN 2:
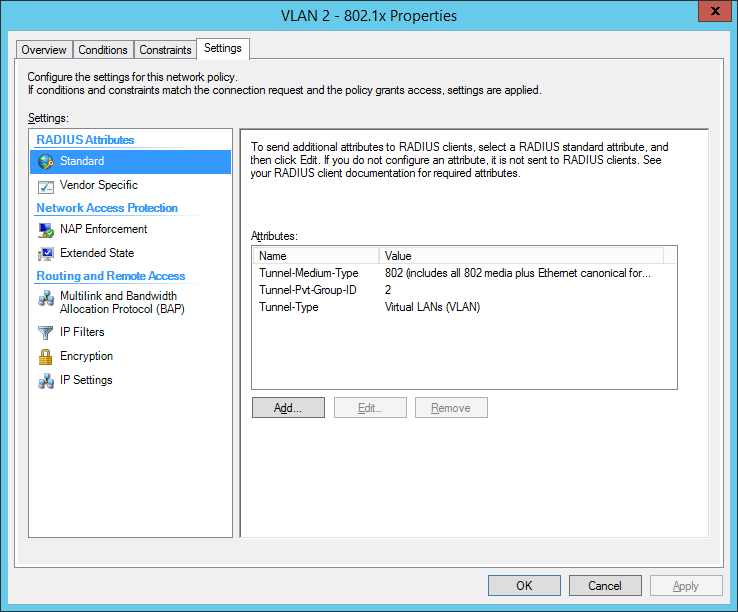
the final dot1x configuration in the NPS:
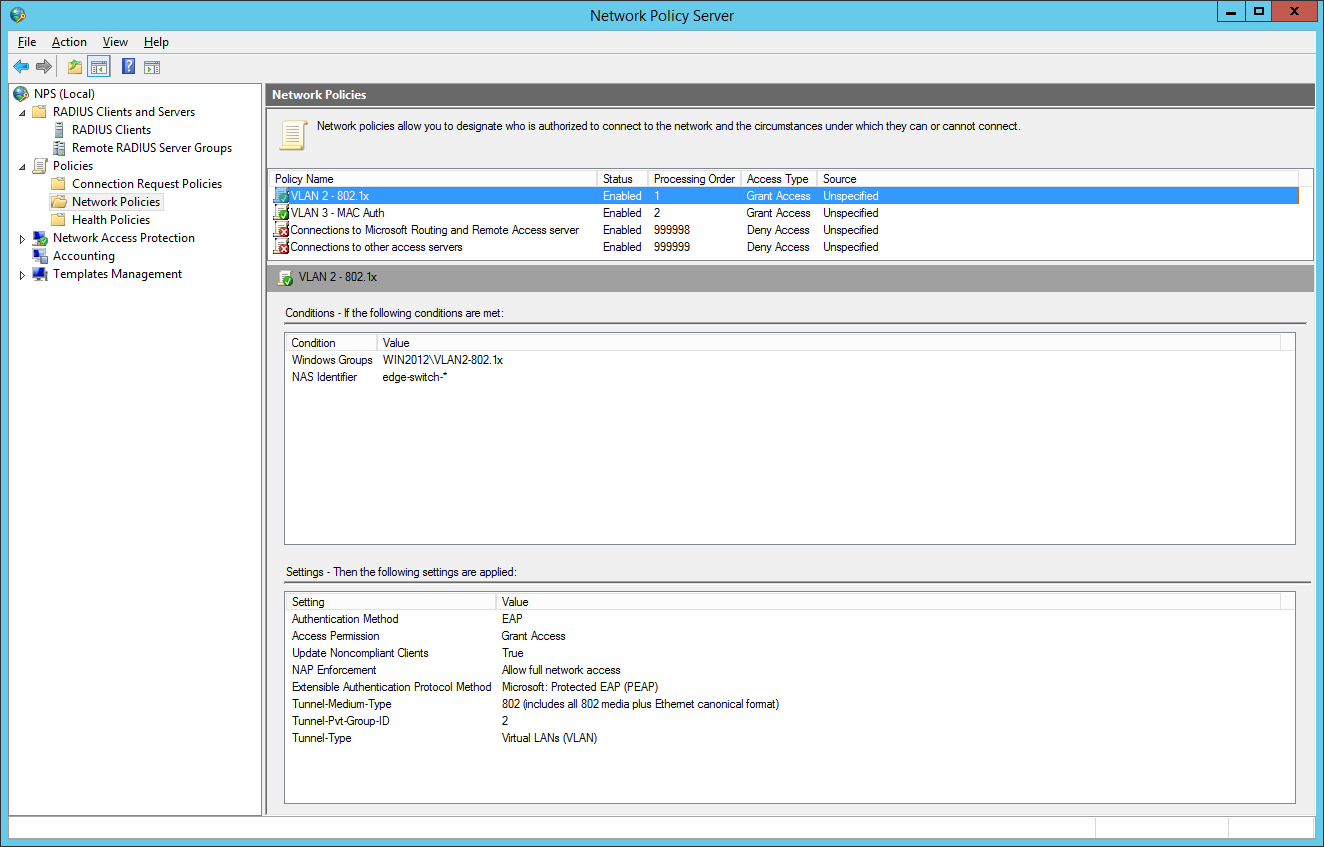
the second network policy is for the mac-based authentication:
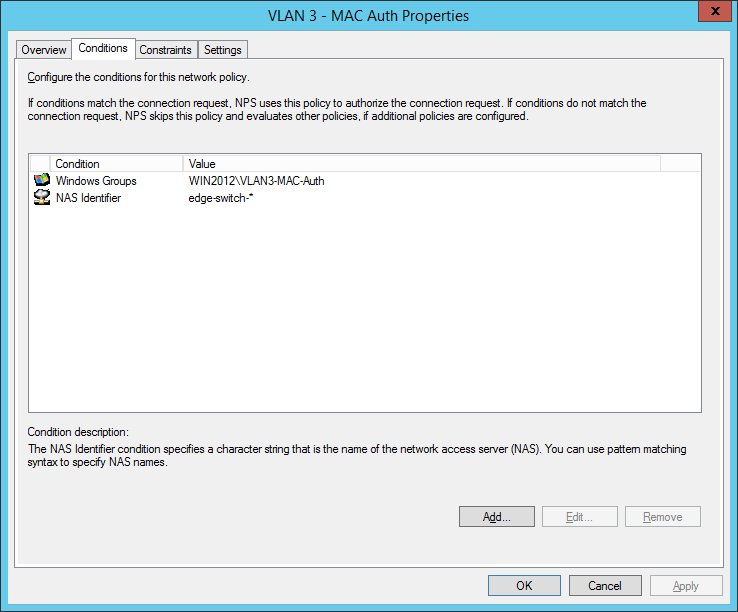
Comware switches are sending MAC-Auth-requests via PAP (maybe you know how to change it to CHAP):
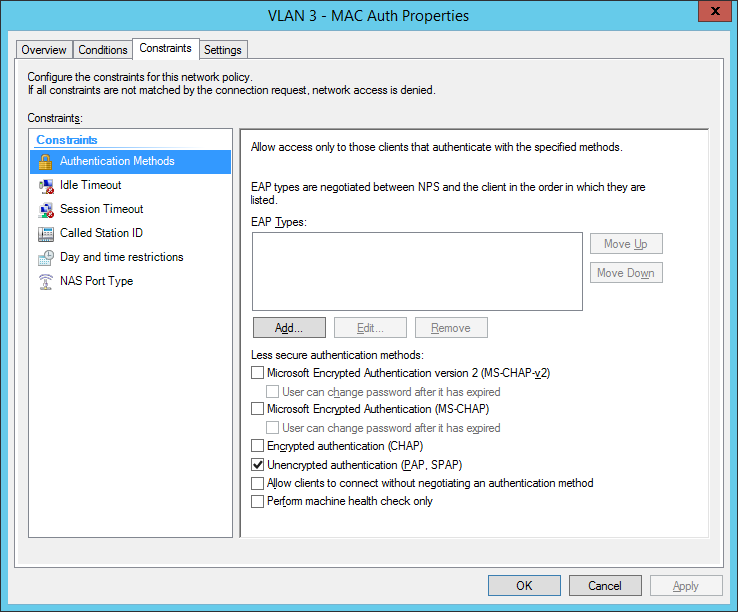
final MAC auth profile:
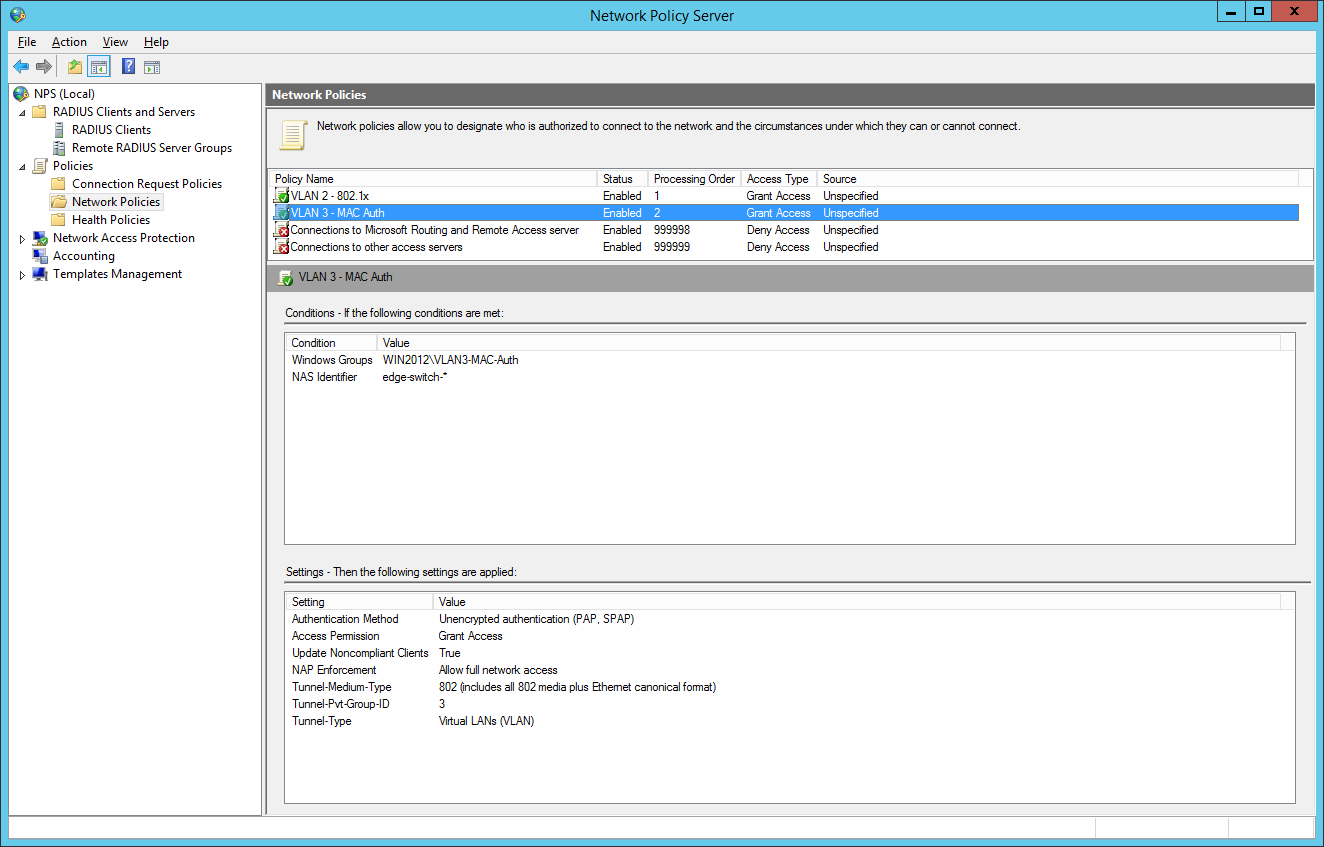
for now we have built up our authentication server. Now let’s go to the switch configuration. You have global configuration parameters and parameters for each interface. The best way is to use interface-range command to be safe at your configuration. Users who cant authenticate, will be forced to VLAN 999 (quarantine VLAN with no gateway). Here are the global parameters with explanations inline:
now we will configure the interfaces: Added 2 entries
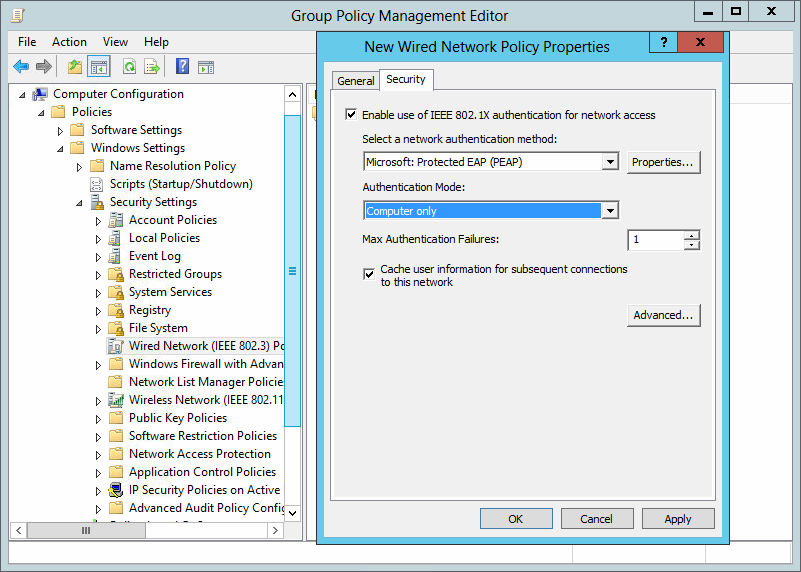
the last part is to configure all windows clients to send 802.1x auth data to the cable network. I’ve done this via a global group policy. You can find the settings under Computer Configuration / Policies / Windows Settings / Security Settings / Wired Network (IEEE 802.3) Policies:
So how does a working 802.1x-auth looks like?
%Jan 3 01:59:59:531 2013 edge-switch-01 DOT1X/6/DOT1X_LOGIN_SUCC: -IfName=GigabitEthernet1/0/10-MACAddr=0023-2415-42a3-AccessVLANID=1- AuthorizationVLANID=2 -Username= host/PC123.mycompany.local ; User passed 802.1X authentication and came online.
Successful Mac-Authentication of a printer:
%Jan 3 01:31:28:782 2013 de-pad-l19-edg01 MACA/6/MACA_LOGIN_SUCC: -IfName=GigabitEthernet1/0/9-MACAddr=0017-c82d-e9bf-AccessVLANID=1- AuthorizationVLANID=3 -Username= 0017c82de9bf -UsernameFormat=MAC address; User passed MAC authentication and came online.
I tried to draw a flow chart which shows the authentication process, I hope it’s ok for you :)
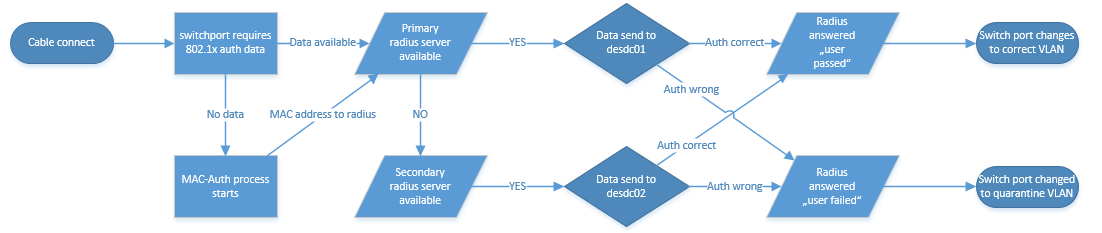
Do you have questions? Feel free to write them into the comments and I will try to answer.

Have a nice and sunny day!
/edit: If you can’t see success and failure events, follow this instruction: NPS / Radius Server is not logging
/edit 2018-05-14: I corrected the global and interface configuration, we had problems with the old configuration
12 Responses
Thanks for this, I need to setup dynamic VLAN assignment in the near future but for Juniper equipment.
This at least gives me a good starting point, thanks for the write up.
Many thanks for the perfect tutorial on How to use 802.1x/Mac-Auth and dynamic VLAN assignment. Many of us can take help from it. Really nice.
Nice write-up. This was a great starting point for configuring the base for dynamic polices. Thanks!
hi Mike, how ‘s about hybrid port with voice-vlan? does it work?
thanks Tung Duong
we had several problems with this config, currently we are investigating hyprid ports with “port security” command. I will update this post if we have prooved this version.
Can you tell me why I would do this over conventional static VLANs? What are the benefits radius dynamic VLANs?
we have customers which want to divide the network for clients, printers and “special devices”. So you have different group/radius-policies to directly place the devices in the right VLAN. Dynamic VLAN is only a bonus feature which you can use. Of course, you can use only the 802.1x and Mac authentication for security purpose.
I’m on the desktop side of things, so apologies if I use any incorrect terminology here.
Our Infrastructure team are looking at introducing 8021x in our schools. They have a test setup where all 8021x devices pick up a data centre VLAN regardless of which building they’re in – eg 10.100.50.
Each building WIRED has its own unique IP – SchoolA=10.120, SchoolB = 10.130 and so on.
I’ve asked if the 8021x setup can be where 8021x devices in SchoolA will get 10.120.50; SchoolB will get 10.130.50
This would allow us to easily determine which building LaptopA actually is, in the same way as we can with our wired desktops. It also saves on SCCM boundary issues causing applications/updates to be pulled over the WAN rather than the LAN.
It’s been suggested that this may not be possible. Could someone confirm this?
Thanks in advance.
Hello! This is of course possible!
My idea (with examples):
SchoolA=10.120 (Location: Chicago) SchoolB=10.130 (Location: Dallas)
So at Chicago you will have VLAN 333, every device is getting an IP address with 10.120.x.x. At Dallas every device in VLAN 333 is getting an IP address with 10.130.x.x. So the VLAN ID “333” is the same at every school but the DHCP scope and default gateway has it’s own address. So the device is getting the VLAN 333 at every location but another IP address. It’s very simple.
It’s not working if all schools are connected via Layer2 so VLAN333 can’t be a “standalone VLAN” at each geographical location.
Ask me any questions, I will try to help you.
- Pingback: 802.1x, MAC-Authentication and VLAN assignment at ProCurve/aruba Switches – Network Guy
- Pingback: Port Auth, Dynamic VLAN and Radius | samuelnotes
- Pingback: HPE Comware problem with mac authentication and printer - Network Guy
Leave a Reply Cancel reply
Click on the button to load the content from jetpack.wordpress.com.
Load content
This site uses Akismet to reduce spam. Learn how your comment data is processed .
Certificates

Post Categories
Post archives, recent posts.
- Sophos UTM 9.712-13 HA update problem 14. November 2022
- Sophos UTM 9.712-12 update released 24. August 2022
- Aruba OS Switch automatic vlan assignment for aruba APs 5. May 2022
- Sophos UTM 9.711-5 update released 22. April 2022
- Sophos UTM 9.710-1 update released 20. March 2022
Recent Comments
- Sophos Ssl Vpn Client Anmeldung - Login and Portal on Auto-Logon with Sophos SSL VPN Client (OpenVPN)
- Russell on Install Sophos UTM from USB Stick
- arno on Problems with incoming mails
- GigaTech IT on Installing Realtek Driver on ESXi 6.7
- Sophos User Portal Login Ssl Vpn - Online Login on Auto-Logon with Sophos SSL VPN Client (OpenVPN)
Franky’s Web Website from my friend Frank. News and Tricks about Microsoft products, primarly Exchange Server
Copyright by networkguy.de
Imprint · Privacy Policy

COMMENTS
To dynamically assign VLANs to bridge access ports using the 802.1X device authentication flow: In Director view: Select the Administration tab in the top menu bar. Select …
This document describes the concept of dynamic VLAN assignment and how to configure the Catalyst 9800 wireless LAN controller (WLC) and Cisco Identity Service Engine …
Dynamic VLAN assignment. You can configure the RADIUS server to return a VLAN in the authentication reply message: On the FortiSwitch unit, select port-based …
Dynamic VLAN Assignment. In lieu of CoA, MS switches can still dynamically assign a VLAN to a device by assigned the VLAN passed in the Tunnel-Pvt-Group-ID …
The 802.1x protocol is used for network access control. For devices like printers, cameras, etc. we will use mac-authentication as a fallback. We will also use dynamic VLAN assignment for the connected ports. Our radius server will be …
The IEEE 802.1X VLAN Assignment feature is automatically enabled when IEEE 802.1X authentication is configured for an access port, which allows the RADIUS server to …
After successful IEEE 802.1X authentication of a port, the RADIUS server sends the VLAN assignment to configure the device port. The RADIUS server database maintains the …